Estimated read time: 5 minutes
The online safety is getting more and more critical in the IT world. Businesses rely on their data and systems for a variety of functions. Still, now it's becoming evident just how vulnerable they are - both externally from hackers through online attacks or internally where employees could find ways into sensitive information!

If you are a founder or an executive, you have a lot of responsibility on your shoulders. Not only do you need to worry about the day-to-day running of your business, but you also need to think about the future and ensuring that your business is safe online.
How to Stay Safe Online with the Rise in Cyber Threats?
It can be challenging to keep up with the latest security threats and online scams, but we'll share six tips on how to make your online business more secure. By following these tips, you'll be giving yourself and your business the best chance for success. So let's get started!
1. Protect your internal systems and resources
Sensitive information needs to be protected. Make sure that it is stored securely and only accessed by authorized personnel. Online criminals will always be trying to get in. Unauthorized access to personal or financial information can lead to negative consequences, such as identity theft, data breach or fraud.
Therefore be very careful when identifying which internal systems and resources should be accessible from the internet whether the protection is sufficient.
👉 By limiting this surface area, you make gaining entry difficult, if not impossible!
2. Limit access only to necessary services
Every module (such as a process, user or program) must be able to access only the information and resources it needs for its legitimate purpose. The principle of least privilege means that a user account or process should only have those rights and permissions necessary to do its job.
For example, suppose a user's job requires frequent updates on an internal customer database. In that case, they should be able to do so without being given full privileges so that their actions can't potentially compromise other areas within your organization or cause breaches from outside sources who have obtained unauthorized entry into these systems.
👉 By limiting access only to those services your employees really require, you can help keep things organized while saving on time and cost!
3. Secure your internet connection when working remotely
While it may seem like there are no easy solutions to the cybersecurity problems administrators face, new technology offers a way forward. The way to increase the security of your connections between employees´ devices (notebooks, mobile devices) and company resources is by using security software such as VPNs (Virtual Private Network).
VPNs are a great way to increase your security. They work by establishing an encrypted connection between you and internet server so that nobody can see what information is being sent or received on either end, not even near-by hackers!
Setup these security measures in your company, especially if your employees work from remote places with public wi-fi like internet cafes, airports, trains, .... or from home.
👉 Using secure connection tools can create an easy way for employees across different departments work in sync with one another more effectively than ever before - because these small changes add up over time!
4. Monitor your network for suspicious activity
Suspicious network activity is not limited to a few specific behaviors. This could include out-of-the ordinary access patterns, database activities or file changes which may indicate attack by hackers looking for personal information like passwords and usernames - so it’s important not only monitor what you let through but also who has access!
This will help identify any potential online threats before they can do damage on the network or otherwise cause a data breach. Analysing connections is highly recommended to your servers and any other source that may have been used in an attempt of infiltration.
👉 Can´t be too careful, so analyze every connection to be sure!
5. Use endpoint protection solutions
Endpoint protection solutions are a type of software that monitors your computer and provides extra defense against malware, ransomware attacks. Not only computer is at risk but all client devices such as cell phones, tablets, laptops, internet-of-things.
The evolution of endpoint security has been a shift from antivirus software to more advanced, comprehensive defense. The next generation of antivirus software needs to be intelligent, dynamic and fast. It has a real-time connection with other security solutions so it can share information on online threats as they arise across networks.
👉 Endpoint protection solutions will keep your devices safe, so you can work without worrying!
6. Control access policy
The key to ensuring that you have an effective access control policy in place for protecting valuable items like computers or other business belonging within company premises, begins with implementing proper procedures before any employees are granted entry into restricted areas where they will be working while on site at work.
Your access policy should reflect your organization's needs and security requirements. You can control who has what level or type of privilege, depending on their role in the company - for example head counts might be able to view financial information while others won't have that capability at all!
If an employee leaves or his device gets compromised and account information is stolen, you won't need concerns about him leaking business data as all access permissions must be removed automatically.
👉 Drop the account if the employee leaves company or the device used for access is compromised; it will keep everything safe!
How to Secure Online Connection Optimally
Above are the essential tips on how to protect your online connection. Besides these rules, many supporting tools are available that solve all of those problems for you. In addition, you need to take care of setting necessary controls. With so many rules, controls and tools for securing your online connection available today - it is hard to know where or what exactly you need. The following diagram shows how all of these pieces fit together:
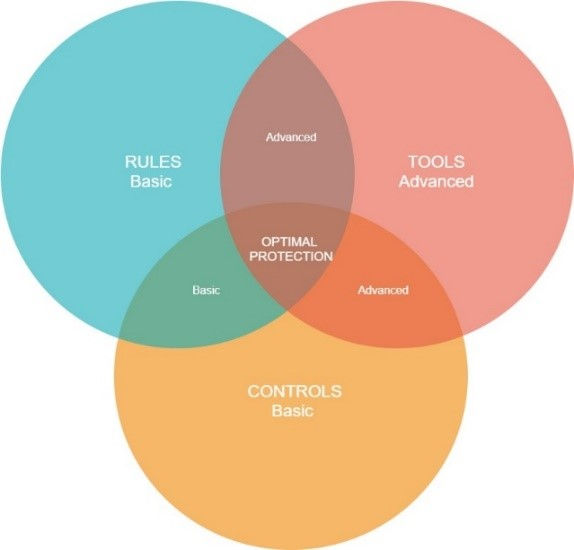
A Few More Internet Safety Tips for Your Business
1. Strong password protection
Strong passwords are critical for any kind of security. Create strong passwords which should be hard to guess, unique across all accounts you have, and contain numbers or special characters so they're not pronounceable when typing on an English keyboard!
There are many benefits to use a password manager. They save you time by generating complex passwords for all your online services in one place and keep track of which ones have been used before.
2. Two factor authentication
Two-factor authentication is a great way to add an extra layer of security for your accounts. Multi-factor authentication (MFA) is an electronic method that requires users to provide two or more pieces of evidence before they can access their accounts. This includes knowledge (something only the user knows), possession (something only the user has), and inherence (something only the user is).
3. VPN alternatives
If you want to be one step ahead, you will not settle with a VPN. There are various VPN alternatives: based either on ZTNA (Zero Trust Network Access) or on SDP (Software Defined Perimeter) concept.
In a world where employees are increasingly working from home and other remote locations, companies have been turning to modern cloud-native security solutions such as zero trust network access in order to make remote work environments more productive and secure.
In term of security, the idea of Zero Trust is to never trust anyone, even when it comes inside your own security perimeters. You have prove who you are and what resources access before being given permission for certain things like sensitive data or system functions
ZTNA solution with these benefits: no additional latency, higher level of security, easy setup, independent on device/computer/company architecture might be a solution you are looking for. Try out or just explore more.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
Why is internet security important?
Internet security is important to keep cyber attackers from accessing sensitive information. Otherwise the business might risk the unwanted security breaches or the spread and escalation of malware, etc.
How to stay safe online while running online business?
Protect your internal systems and resources, limit access only to necessary services, secure your internet connection when working remotely, monitor your network for suspicious activity, use endpoint protection solutions and control access policy.
How to increase safety of your online business?
Use strong password protection, use two factor authentication and test some of the VPN alternatives based either on ZTNA (Zero Trust Network Access) or on SDP (Software Defined Perimeter) concept.





