Estimated read time: 5 minutes
The pandemic has changed how companies work and this change is here to stay. As the world emerges from the effects of Covid-19 and employees resume working at the office, there’s still a huge chunk of the workforce who prefer a hybrid work model. This emphasizes the need to provide secure remote access for the organization.
Secure remote access is important to protect the company’s intellectual property and sensitive data. It also increases employee productivity and enhances the organization's competitive advantage. When employees can work securely anywhere, companies are more confident in delivering their goals and creating innovations.
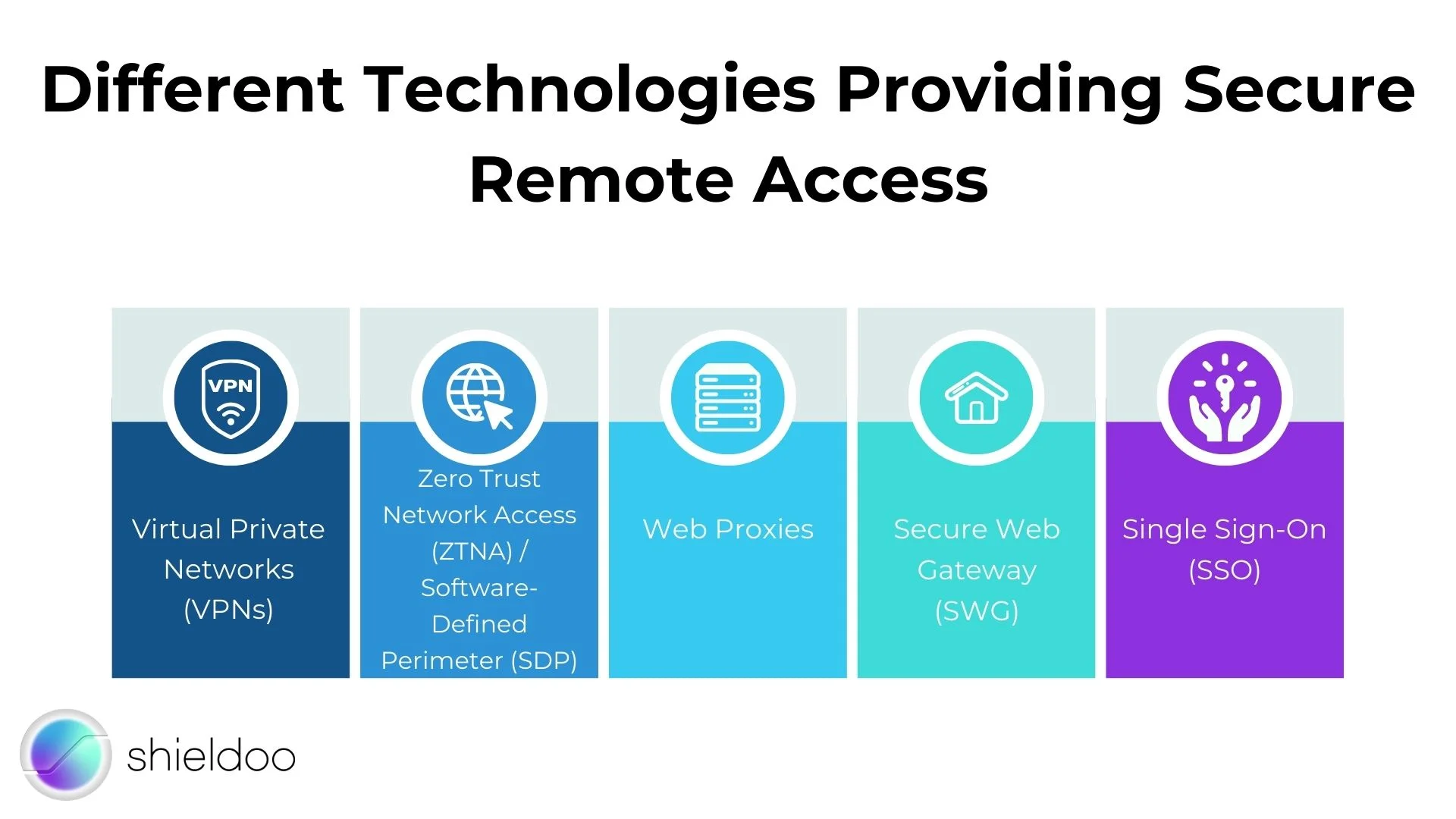
Different Technologies Providing Secure Remote Access
Different technologies work together to ensure the security of today’s remote workforce. Choosing one depends on the organization's size and the ratio of onsite to remote workers. Here are some commonly used secure remote access technologies:
- Virtual Private Networks (VPNs)
VPN provides secure remote access through an encrypted tunnel that connects the user’s device to the organization's IT network. They keep the user’s location private and provide privacy and anonymity. VPNs are deployed using client software on an endpoint or a clientless web browser where the user navigates to an HTTP/HTTPS portal.
- Zero Trust Network Access (ZTNA) / Software-Defined Perimeter (SDP)
ZTNA provides secure remote access through pre-defined access control policies. By default, all users are denied network access. Network administrators set up user permissions specific only to applications and services the user needs to perform their job.
- Web Proxies
Web proxies work by terminating the connection between a user and the network and then sending another anonymous connection request to the end destination. This is a popular solution but only works for web requests and cannot encrypt all device traffic.
- Secure Web Gateway (SWG)
Users are protected from malicious web threats by connecting to an SWG instead of directly to a website.
- Single Sign-On (SSO)
SSO allows users to access multiple network applications using only one login credential. This is convenient for users but not ideal as it’s prone to malicious attacks. SSO technologies should be used together with other security strategies.
Choosing the Right Tools
Implementing remote access security is as easy as purchasing and setting up the right tools. However, there are many tools available in the market and it can get confusing to choose the best among them. There are also other factors to consider, such as the availability and skills of the IT team who will be tasked to maintain these technologies.
When choosing a secure remote access tool, here are several tips to help you make a wise decision.
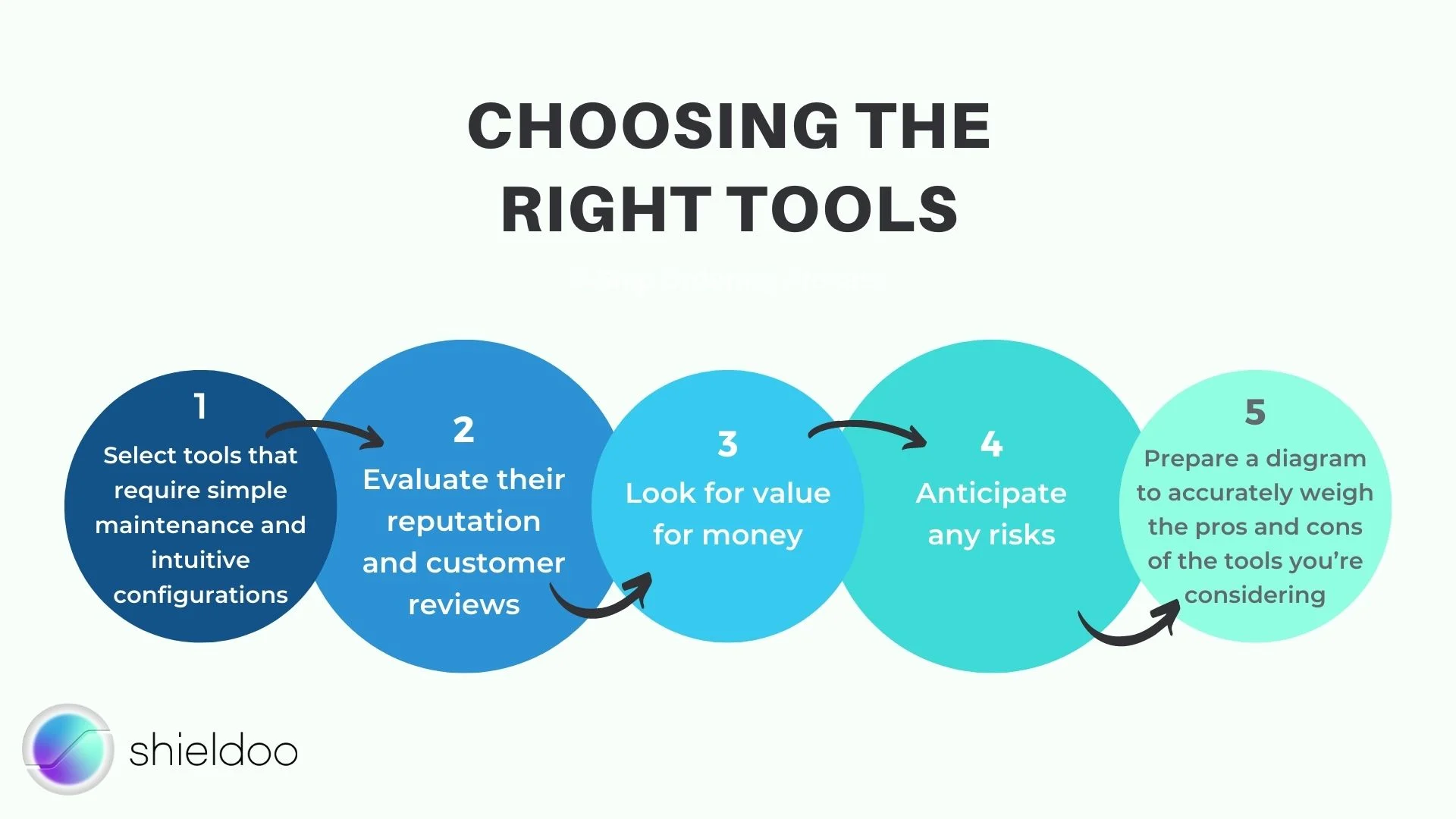
1. Select tools that require simple maintenance and intuitive configurations
Some tools can be very complex and technical to set up and maintain. To implement it successfully for your organization, you need skilled and dedicated IT professionals. Sometimes, these tools would also require a bit of technical know-how from your employees. If it becomes difficult to use, it would be detrimental instead of beneficial. Employees would end up frustrated and unproductive.
In contrast, tools that are simple to set up and maintain will get more work done. Remember that employees are working remotely and you don’t want them to waste time figuring out how to use the tools that are supposed to make their work easier. This also frees up valuable time from your IT team and enable them to work on other activities.
Simple tools don’t mean lesser security. Find ones that work just as well but are more intuitive.
2. Evaluate their reputation and customer reviews
Go for tools that are tried and tested by other organizations within your industry. Your company’s data security is at stake and you should only work with companies with a proven track record.
When evaluating their solutions, they should be transparent and if needed, provide additional resources for validating their claims. You should also be able to check their security policies to be certain that your data is treated confidentially and securely.
3. Look for value for money
When choosing remote access security tools, consider their upfront fees and the cost of maintenance. Include additional costs if you need to hire an extra person or a team for setup and implementation.
Consider the time and financial resources required for training your organization. Factor in any requirements for additional IT equipment like additional routers. Depending on the tools you select, the extra costs will be different.
Some tools also have extra features that your company doesn’t need. Scrutinize those, as they could waste your money.
4. Anticipate any risks.
No system or tool is fool-proof despite their claims. There would always be risks involved either from unintentional misconfigurations by employees or intentional malicious attacks from suspicious entities. When choosing a tool, consider the risks that would potentially arise and work on countermeasures to mitigate them.
By anticipating risks and being prepared, you increase the chances of success for your chosen tools and technology. It’s always better to be over-prepared than to be caught in surprise.
5. Prepare a diagram to accurately weigh the pros and cons of the tools you’re considering.
Having a visual representation of the benefits and disadvantages of the tools vis-à-vis the important factors you must consider is helpful in decision making. You can use a diagram similar to the one below.
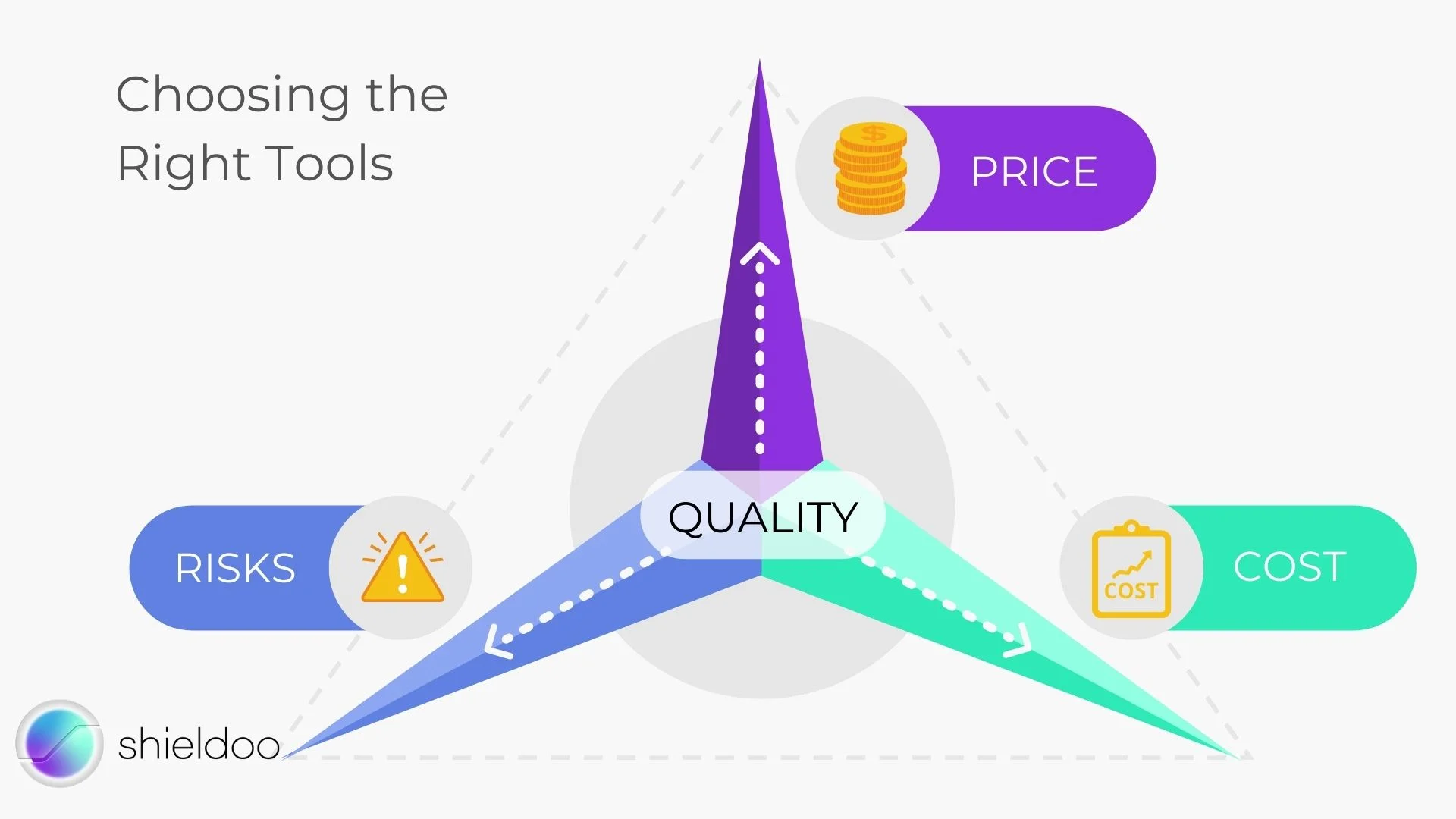
Try to find the balance between low risk, low maintenance cost, and a fair price to arrive at a good quality product.
Striking the Balance Between Cost and Quality
Discover a tool that helps secure your network without breaking your budget. With Shieldoo™️, a next-gen cybersecurity solution, you can confidently implement a security solution that protects your organization from internal and external threats. The Shieldoo™️ secure network is designed for the needs of the hybrid workplace. Get in touch today to learn more.

Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What is secure remote access?
Secure remote access is important to protect the company’s intellectual property and sensitive data. It also increases employee productivity and enhances the organization's competitive advantage. When employees can work securely anywhere, companies are more confident in delivering their goals and creating innovations.
What technologies can provide secure remote access?
Virtual Private Networks (VPNs), Zero Trust Network Access (ZTNA) / Software-Defined Perimeter (SDP), Web Proxies, Secure Web Gateway (SWG), Single Sign-On (SSO), ...
How to choose the right tool for secure remote access?
Select tools that require simple maintenance and intuitive configurations, evaluate their reputation and customer reviews, look for value for money, anticipate the risks and prepare a diagram to accurately weigh the pros and cons of the tools you’re considering.





