Estimated read time: 4 minutes
Running a business means having to constantly deal with customer data. Marketers rely on data to determine what customers need, how they behave, and how their pain points can be addressed. Simply put, customer data is a lifeblood for any business.
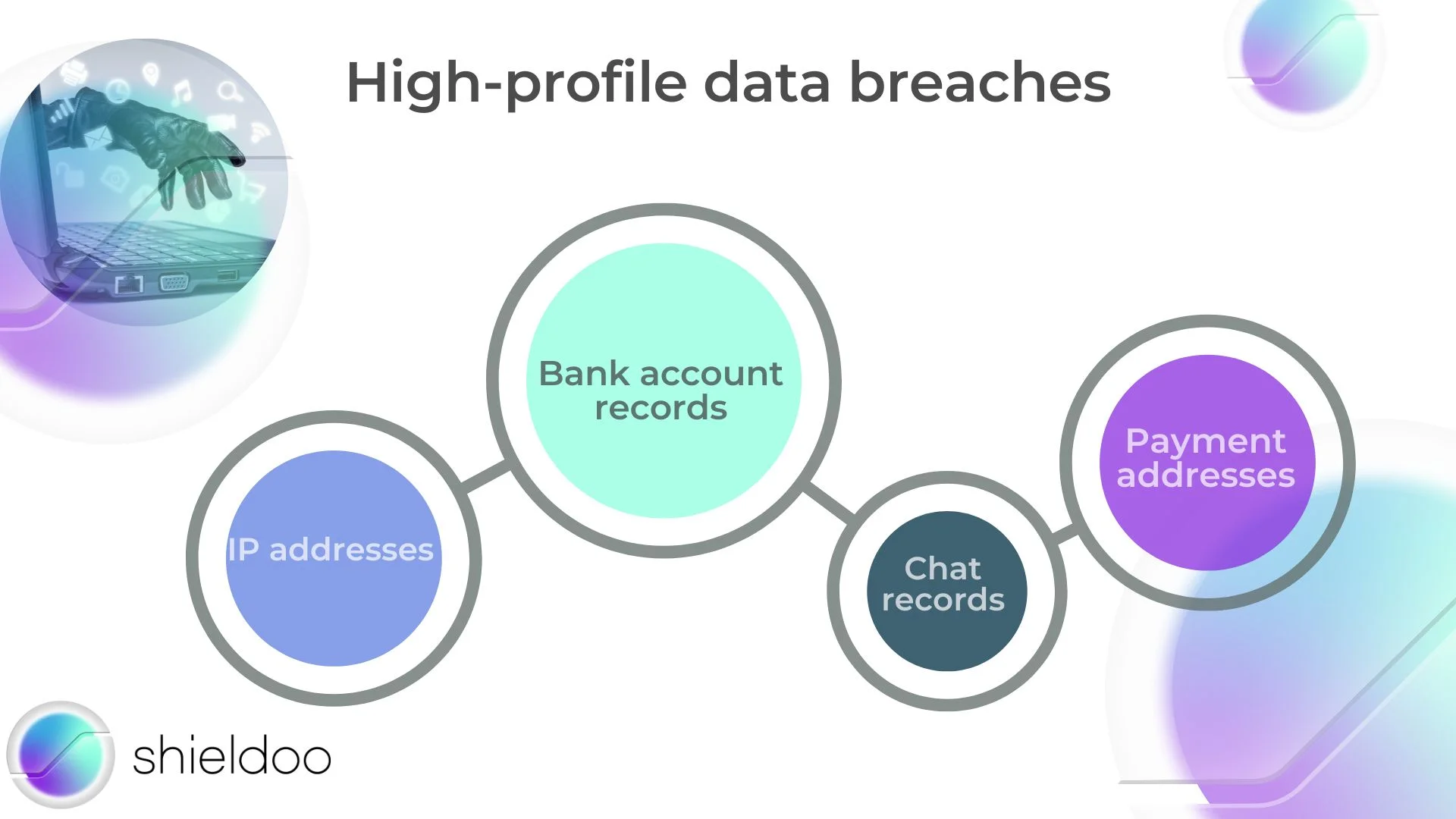
However, with the recent high-profile data breaches, customers have become concerned about their privacy. Sensitive data, such as IP addresses, chat records, payment addresses, and bank account records, were leaked.
How can you protect your customers and their data from such attacks? How can you maintain your customers’ faith in your business?
When handling customer data, especially personally identifiable information (PII), you need to have a robust data protection strategy for implementing data security and privacy.
Here are some of the best customer data protection practices you can apply.
How to Keep Customer Data Safe
There’s a pressing need for companies to prioritize customer data protection. As such, you need to regularly evaluate and revise your data privacy policies accordingly.
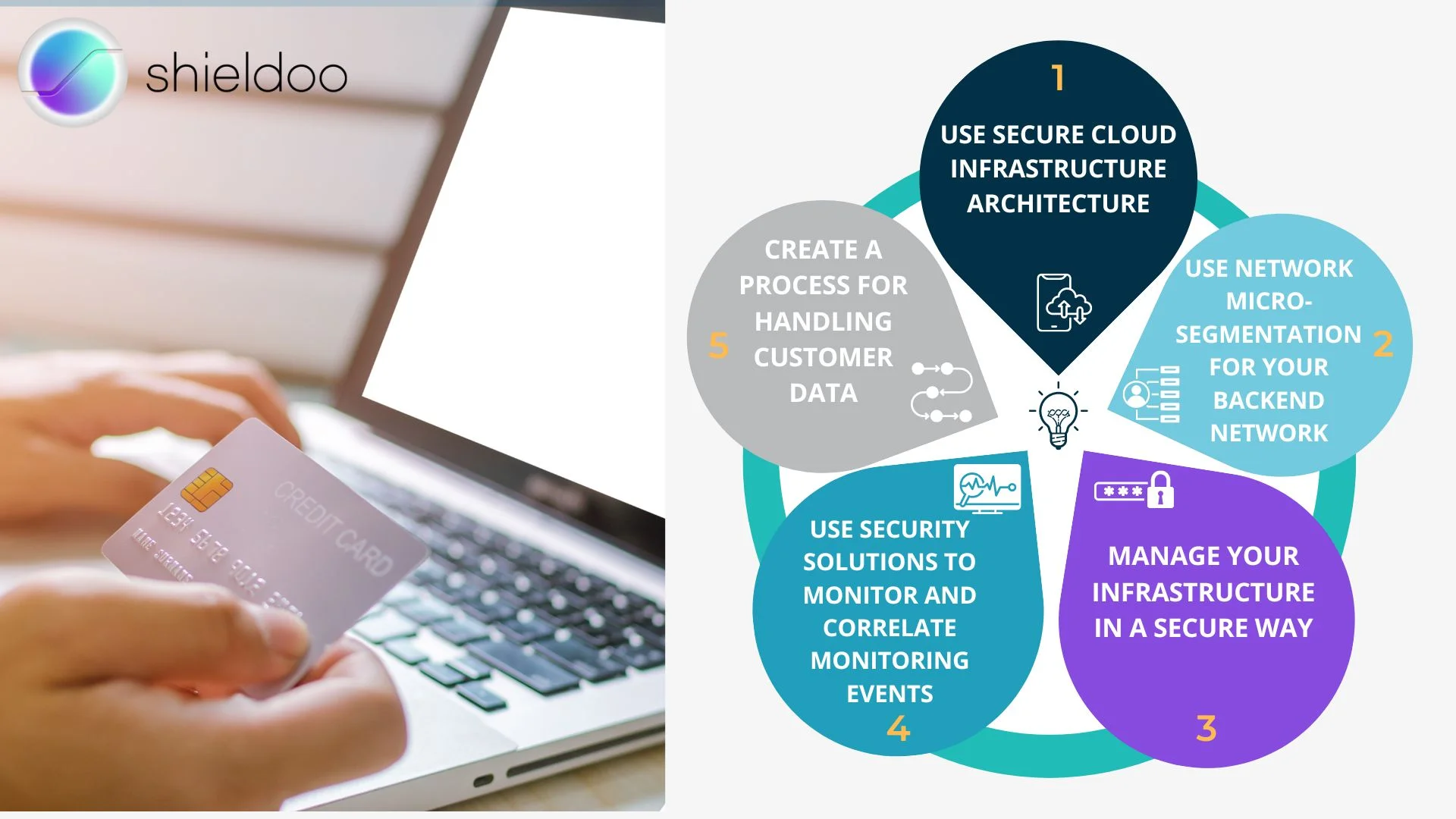
1. Use secure cloud infrastructure architecture
Refrain from accessing customer data or platform databases using a public or open connection. An unsecured network, like public Wi-Fi, can leave you vulnerable to cyberattacks, as hackers can use an open network to spread malware or access your database.
To safely access your database, you need to have a secure cloud infrastructure architecture in place. Cloud security architecture is comprised of hardware and software that are designed to protect not only data but also your systems, particularly within the cloud platform you’re using.
2. Use network micro-segmentation for your backend network
Network micro-segmentation or host-based segmentation limits the access between components. This security technique divides your data centers into manageable segments that allow administrators to oversee security policies. With micro-segmentation, you’re able to better isolate attacks and prevent cyberattacks from affecting other network components.
3. Manage your infrastructure in a secure way
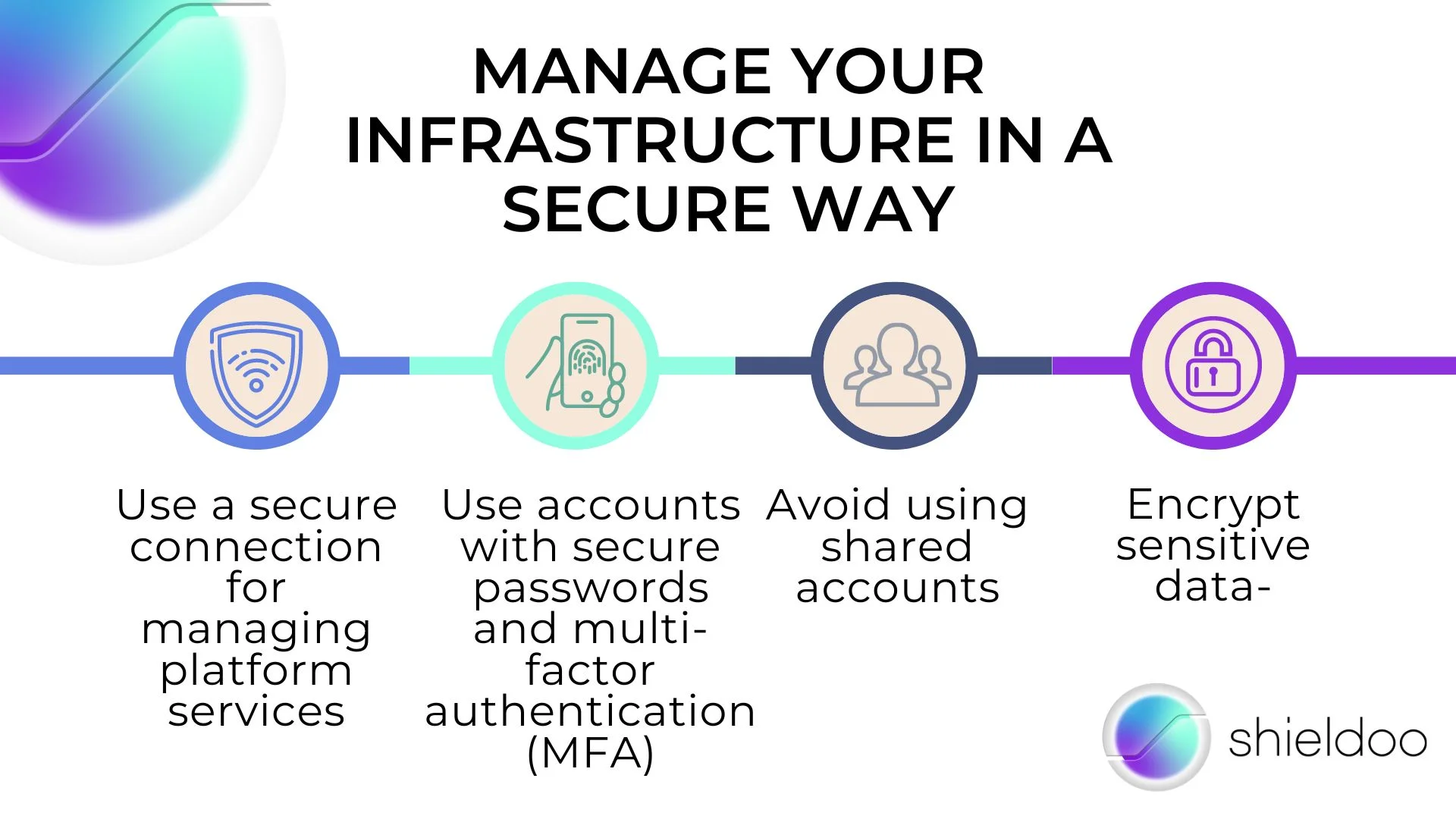
- Use a secure connection for managing platform services
If you’re accessing data or managing database platforms, it’s best to use encrypted or secure connections. With a secure connection, the data that gets relayed from your networks is encrypted with a secure key, which prevents anyone without access to the key from reading your data.
- Use accounts with secure passwords and multi-factor authentication (MFA)
Aside from using a virtual private network (VPN) to protect your network, you can beef up your security measures by using accounts with secure passwords and applying multi-factor authentication as an added layer of security. If an attacker gets a hold of your password, the MFA’s additional token prevents them from gaining total access to your database.
- Avoid using shared accounts
Shared accounts may be essential for your organization, but they can be compromised. Given that multiple people across teams or departments use them, they need to be controlled. If you absolutely need to have shared accounts, make sure that they’re created for a specific purpose and have clearly-defined roles.
- Encrypt sensitive data
Data encryption prevents attackers or unauthorized users from accessing your data, enhancing privacy and confidentiality. Encryption uses a secure or secret key and only the ones who have access to the key can read the encrypted data.
Use security patterns to encrypt security-relevant data in your database and leverage relevant technologies to avoid data breaches in case you lose your data or backups.
4. Use security solutions to monitor and correlate monitoring events
Security Information and Event Management (SIEM) systems let you create a secure monitoring environment with proactive functions. It allows for real-time monitoring and analysis of security events, enabling you to efficiently determine any potential threats and vulnerabilities before they happen.
5. Create a process for handling customer data
How you handle customer data during usual operations can help keep your customers’ sensitive data secure. Your protocol should identify key steps on how you can protect data, protect or regulate access, and make evidence of relevant service actions.
Take proactive measures to protect your customers’ data. The Shieldoo™️ secure network delivers a zero-trust approach that’s backed by features such as single sign-on, traffic monitoring, and time-limited access to keep customer data safe.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.

FAQs
How to keep customer data safe?
Use secure cloud infrastructure architecture, use network micro-segmentation for your backend network, manage your infrastructure in a secure way, use security solutions to monitor and correlate monitoring events and create a process for handling customer data.
How to manage your infrastructure in a secure way?
Use a secure connection for managing platform services, use accounts with secure passwords and multi-factor authentication (MFA), avoid using shared accounts, encrypt sensitive data.
How to handle customer data secure?
It is necessary to define steps how to protect data, protect or regulate access, and make evidence of relevant service actions.





