Estimated read time: 6 minutes
Today, I want to share my experience from many projects we did with our customers or during the operation of our solutions. Let us explain you the minimum security basics for cloud infrastructure architecture in a non-expert way.
When trying to design infrastructure architecture in the public cloud, it is a good idea to follow guides published by AWS or Microsoft. In both cases, the framework is called "Well-Architected".
How Can You Approach This Complicated Area?
We can compare these complex technical things to something more usual, for example, some shop with warehouse - let's call it "Avocado company". The Avocado company sells tasty fresh avocados in their shop, and they are storing vegetables in the warehouse close to the shop.
Let's look closer and check how they are working and which risky areas we can discover:
The first area – Identity

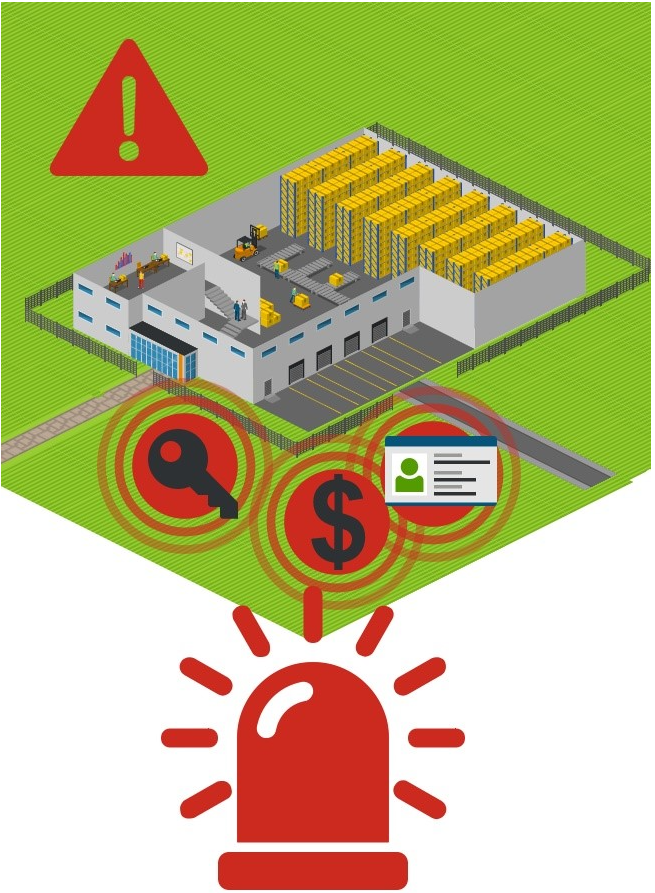
Employees of the Avocado company are using only simple badges even without a photo; there are no strict rules on checking the identity of an employee. If the identity is not strong enough, anyone can enter your system and act like you. It is similar to a user account with a short password or password, which can be guessed.
The second area - Infrastructure Protection
In our parallel to the Avocado company, it means that there is no limitation (or weak limitations) on how to access the warehouse and staffs' area of the shop. In fact, anyone can step into these areas, and there is a very low probability that this unauthorized person will be identified.
The third area - Data Protection
For the Avocado company, "data" means money, they have to ship data securely to the bank, but we can see that data is not appropriately protected during transfer.
The fourth area – Detection
We can see that the Avocado company has no system or process to detect any unauthorized access to the property. So information that something wrong happened can be found later, accidentally.
The fifth area – Response
We can see that the Avocado company is not prepared for situations when something terrible happens; they cannot respond in such cases.
Well, what we can do with this?
First, let's think about how to improve the Avocado company situation.
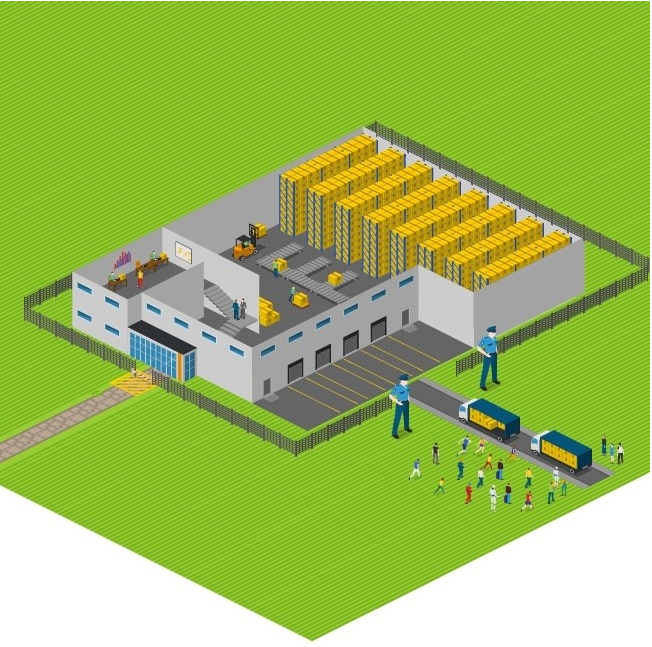
In the identity area, the avocado company has to introduce a more secure process of checking identity and, in fact, more strong identity itself. In our cloud world, we have to use a robust and secure mechanism to secure our identities, like using strong passwords and more authentication factors like SMS or authenticator apps.
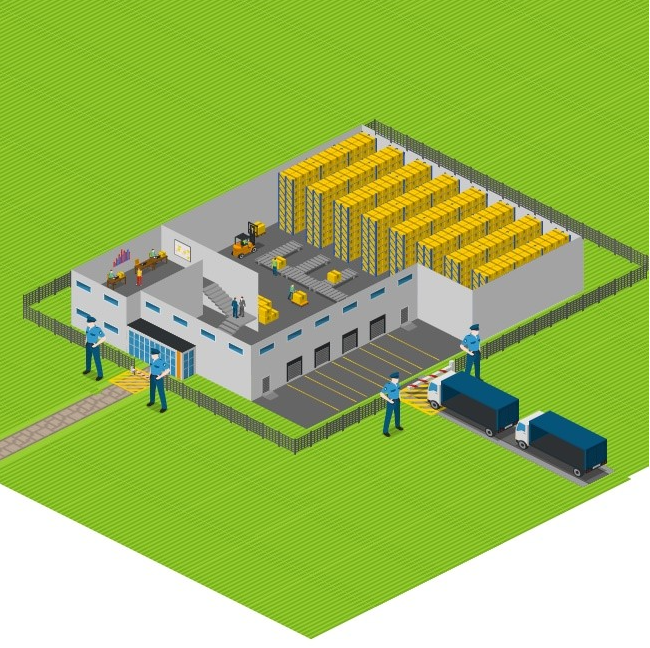
In the infrastructure protection area, the Avocado company has to build a wall or fence around their property with some gates to check who is entering which area of their company. In a cloud solution, we have to build firewall barriers around the solution and strictly control who has access to backend systems or services not used for public presentation. There is good practice to use something called bastion host or some private, secure network like our Shieldoo™️ secure network (mesh) if you want to access backend systems from the outside world.
In the data protection area, the Avocado company must use more secure trucks for delivering money to the bank. In the cloud, we are talking about sensitive data and how to protect them. One layer of protection is encryption to avoid data breaches from physical media like hard disk drives. Another critical area that many companies are underestimating is encryption of backup data, how backups are transferred between the production system and storage, and how everything stored is protected.
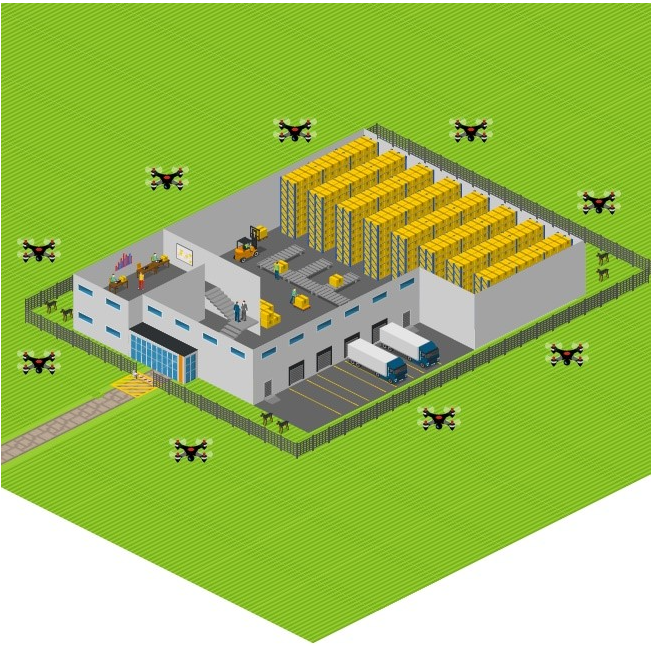
The Avocado company implemented the detection by implementing a unique alarm system supported by drones and collecting data from entrance gates with badge card readers to see who is entering which area and when. In our cloud solution, we can implement many log and event collecting systems data collected in the monitoring system that can be used to detect anomalies. Usually, we can find a very nice solution from cloud providers deeply integrated with their cloud platform.
The Avocado company uses a little old-fashioned approach in the response area, but why not? They use a security company to help them respond when security incidents are detected. But what can we use to protect our cloud solution? Usually, we have to implement some secure orchestration and response system or use embedded cloud infrastructure features for the automatic response. Good practices are limiting access to resources for the user with a potentially stolen identity or switching off the whole solution if a data breach is detected. Your detection shows that hackers are copying data out from your solution.
Try Shieldoo™️
Be careful, don't underestimate security in your cloud solutions. Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What are the security basics for cloud infrastructure architecture?
Identification of the employees, infrastructure protection, data protection, detection of any unauthorized access and response in case of any security breach.
How to improve infrastructure protection in a cloud solution?
To check who is entering which area, we have to build firewall barriers around the solution and strictly control who has access to backend systems or services not used for public presentation. There is good practice to use something called bastion host or some private, secure network like our Shieldoo Mesh if you want to access backend systems from the outside world.
How to improve data protection in a cloud solution?
It is important to protect sensitive data in the cloud. One layer of protection is encryption to avoid data breaches from physical media like hard disk drives. Another critical area that many companies are underestimating is encryption of backup data, how backups are transferred between the production system and storage, and how everything stored is protected.





