Estimated read time: 5 minutes
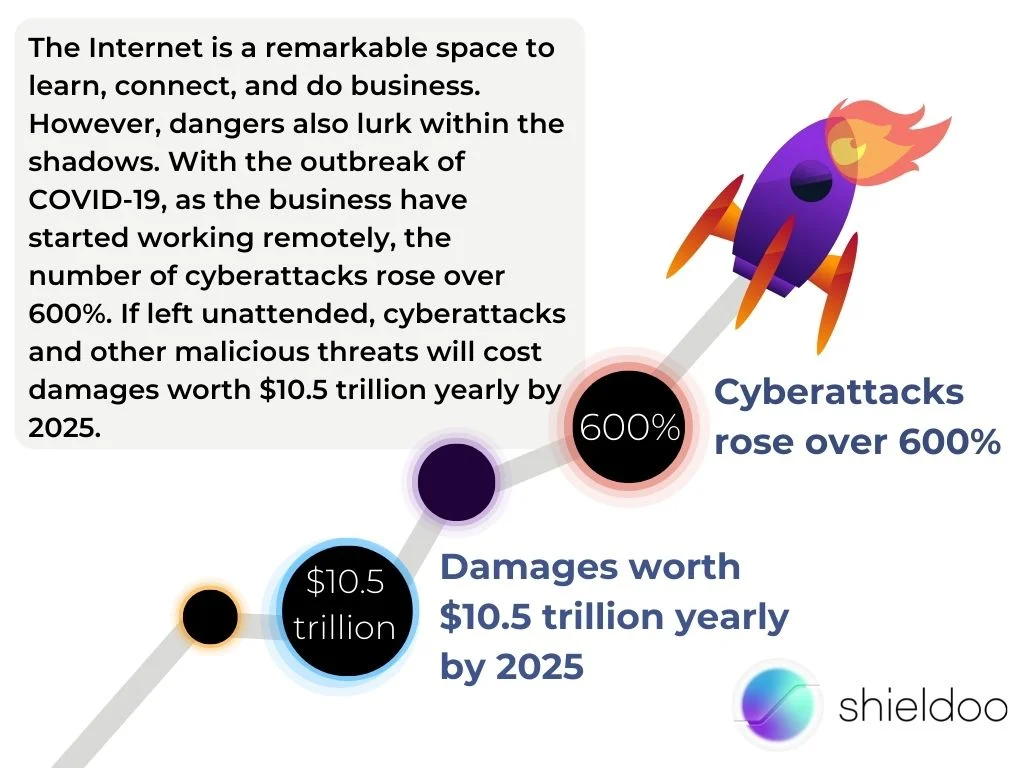
The Internet is a remarkable space to learn, connect, and do business. However, dangers also lurk within the shadows. With the outbreak of COVID-19, as the business have started working remotely, the number of cyberattacks rose over 600%. If left unattended, cyberattacks and other malicious threats will cost damages worth $10.5 trillion yearly by 2025.
A proper cybersecurity plan protects your organization's network from prying eyes and internal breaches. Safeguard critical information and keep hackers away by implementing the following cybersecurity checklist. We recommend adopting these safety measures to keep cyberattacks at bay and educate employees on the importance of cybersecurity.
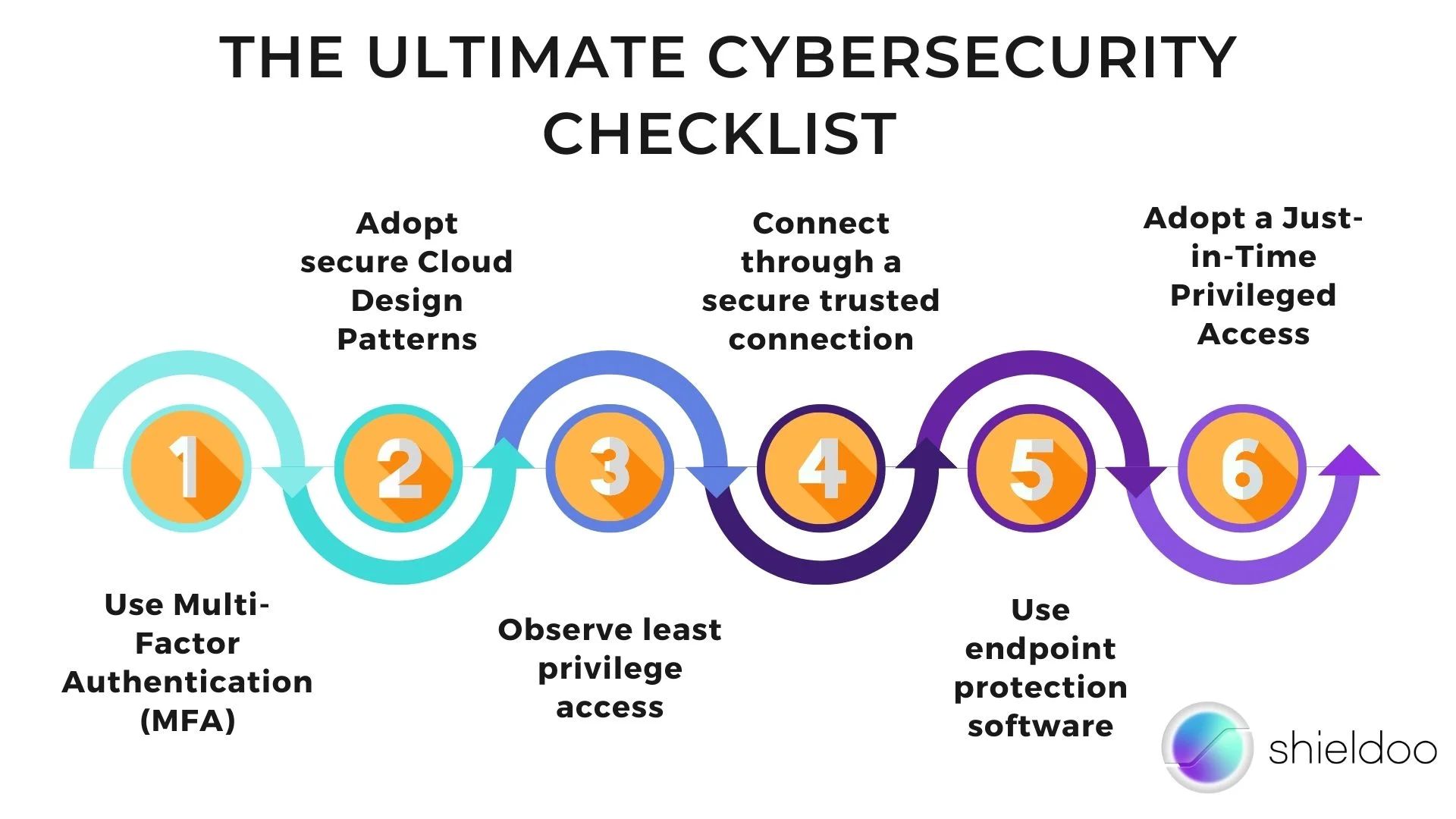
The Ultimate Cybersecurity Checklist to Protect Your Network from Cyberattacks
1. Use Multi-Factor Authentication (MFA)
Multi-factor authentication is essential in observing a strong and trustworthy identity and access management policy. MFA adds multiple security layers upon login to review the authenticity of the user and/or device attempting to establish a connection. On top of passwords and usernames, MFA may send verification codes before users can access applications and services on the Cloud.
Microsoft reports that multi-factor authentication can prevent more than 99.9% of cybercrime attempts. This is among the simplest yet most effective measures a business can adopt to safeguard its network from hackers and identity thieves.
2. Adopt secure Cloud Design Patterns
Cloud design patterns are architectural frameworks allowing organizations to build applications and implement security solutions on a cloud computing platform. Cloud computing helps businesses communicate, store data, and accomplish tasks over the Internet. Microsoft Azure, for example, is a cloud computing platform that enables users to implement secure identity and access management (IAM), data backup and recovery, and an overall improvement in IT infrastructure.
3. Observe least privilege access
The principle of least privilege is a security solution that limits a user’s authority in accessing resources on a network. This minimizes the visibility of sensitive data and ensures that only authorized personnel may be granted access to such components on the network.
User accounts with the least privilege access protect the network from cyberattacks moving across the network. On the other hand, users with root access to the network are prone to attracting cyberattacks and internal data breaches.
4. Connect through a secure, trusted connection
Using multiple devices in varying locations often makes connection attempts that are far from safe. Because of this, the health and security of an organizational network may be compromised. Adopt a trusted connection to ensure that access and user activity on the network is encrypted and safely hidden from the public.
Users browsing the web will know a trusted connection is established between their device and the network through an encrypted handshake. They should only engage with websites using HTTPS. A trusted connection is set when the website URL uses HTTPS, and a lock icon appears on the browser’s search bar. But sometimes neither HTTPS does not mean the connection is safe, so precaution is always fundamental.
5. Use endpoint protection software
Endpoint protection software features a range of security applications an organization uses to protect endpoint devices (e.g., PCs, mobile devices, and servers) from malware penetration and other suspicious activity. Your network’s vulnerable endpoints are where cyber attacking often occurs. Hence, safeguarding devices and promoting optimal device health is necessary to tighten security and prevent data breaches.
Endpoint protection software comes in various types. Anti-malware is a popular endpoint security solution that detects and quarantines phishing attacks and ransomware. Another solution is web browser security, where users accessing cloud and web-enabled services are protected by a web security interface detecting suspicious digital certificates and browser extensions. Users will receive a warning before accessing a suspicious link; they may either go back or move to visit the suspicious website.
6. Adopt a Just-in-Time Privileged Access
Just-in-time access is defined as a “true” least privilege security principle requiring users to have just enough authority to access data and perform actions needed for no longer than necessary. With this, user accounts granted enough privilege may access resources, applications, or systems only when necessary and for the least time possible.
Privileged Identity Management (PIM) in Azure AD features complete management and control over the levels of access users are granted within the organization. PIM enables organizations to provide just-in-time privileged access to resources provided by Azure AD. It also supports multi-factor authentication for increased security for every designated role on the network.
Consult with a Team of Cybersecurity Experts

Cybersecurity is of utmost significance as the Internet has become a significant avenue for business transactions and negotiations. Mitigate the risk of potential data breaches through prevention offered by various security solutions. Shieldoo™️ presents a next-generation security solution perfect for any private network.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What is a cyberattack?
Cyberattack may be defined as any malicious offensive assault targeted against computer network, information system, infrastructure or personal device. It may be attempt by an individual or an organization.
How to prevent cyberattacks?
It is necessary to try to reduce risk by following steps: secure hardware, protect and encrypt data, use security software, educate employees, promote a security-focused culture,...
What are cyber security solutions?
Cyber security solutions consists of tools and softwares that help protect organizations against cyber attacks. It may prevent application downtime, theft of sensitive data, damage to reputation, etc.





