Estimated read time: 8 minutes
Network Security Defined
Network security involves various technologies, policies, and procedures that protect computer networks and data from unauthorized access, disclosure, disruption, modification, or destruction.

Robust network security defends your data and network against cyber threats like malware, hacking, and data breaches using measures such as firewalls, antivirus software, encryption, VPNs, and access controls. It also involves regular updates and patches to network software and systems to address known vulnerabilities and reduce the risk of successful attacks.
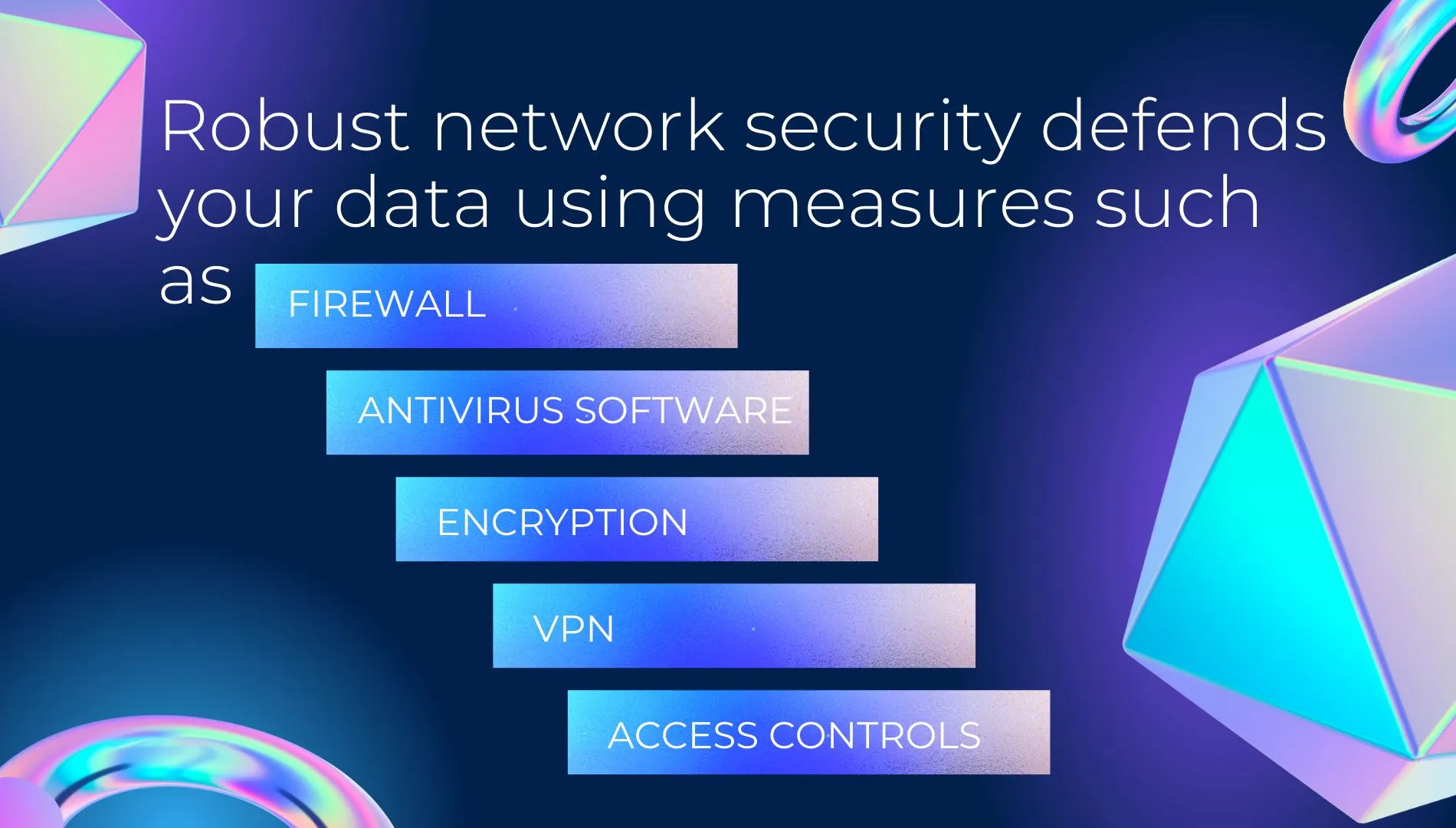
Effective industrial network security requires a comprehensive and multi-layered approach that combines technical controls with user education and awareness. It is essential for protecting the confidentiality, integrity, and availability of network resources and data and for ensuring the continuity of business operations.
How Does Network Security Work?

There are two basic tenets to network security: authentication and authorization. Every user in the computer network must be an authenticated user who’s authorized to access the data they’re accessing.
To accomplish this, network security solutions implement a combination of security tools, protocols, and best practices to protect the confidentiality, integrity, and availability of the IT infrastructure network and its resources.
Network security works as follows:
1. Identifies potential threats and vulnerabilities through security assessments, monitoring, and threat intelligence
2. Implements security measures such as firewalls, access controls, encryption, and anti-malware software
3. Continuously monitors network traffic and events for malicious activity
4. Generates alerts and triggers automated responses to mitigate detected threats
5. Activates a well-defined incident response plan to contain and resolve security breaches
6. Regularly updates and maintains security systems to remain effective against evolving threats
Benefits of Using Network Security
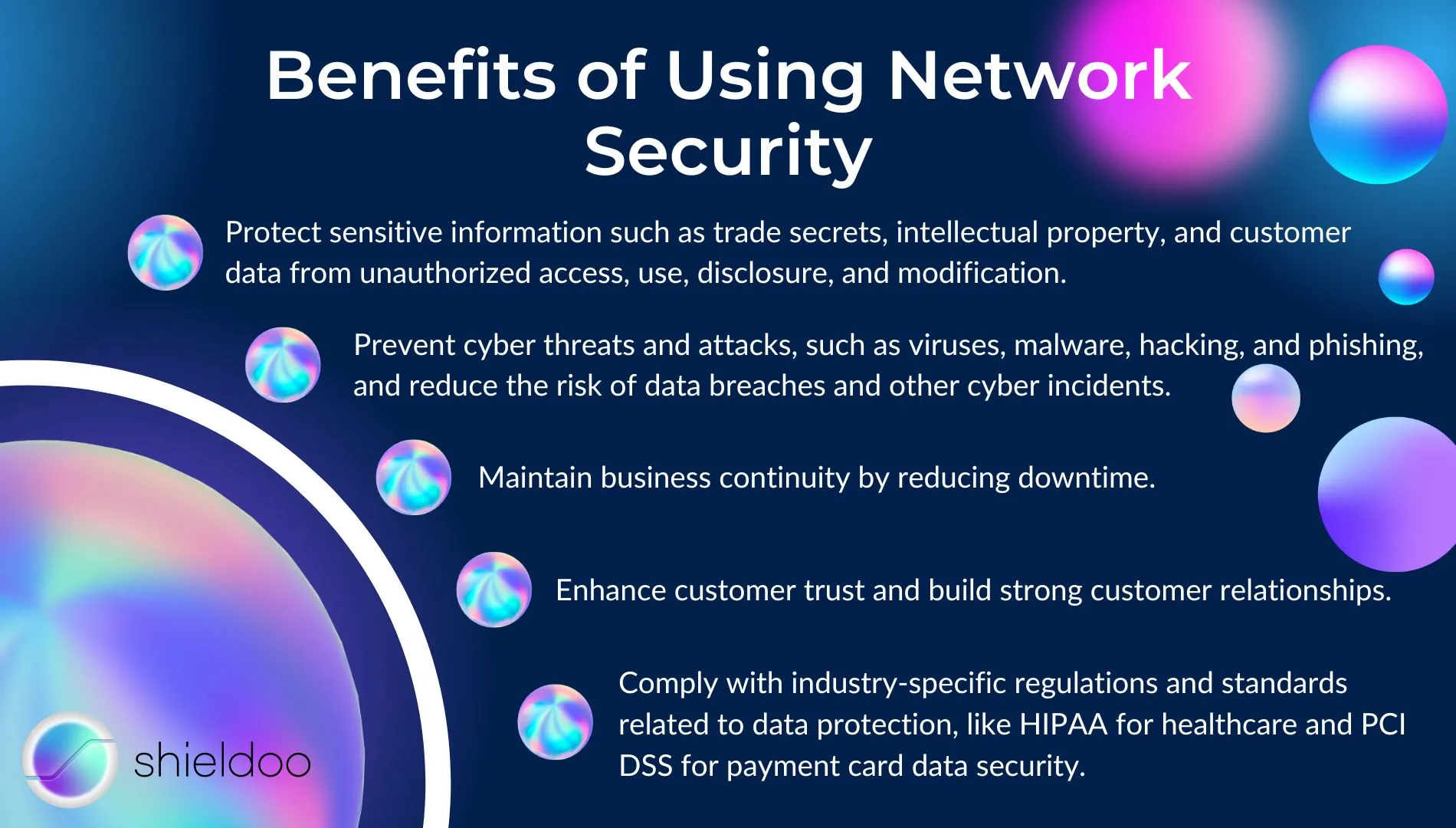
Network security ensures organizations, individuals, and other entities are protected from malicious attacks by unauthorized personnel and potential attackers. Network security services provide the following benefits:
- Protect sensitive information such as trade secrets, intellectual property, and customer data from unauthorized access, use, disclosure, and modification.
- Prevent cyber threats and attacks, such as viruses, malware, hacking, and phishing, and reduce the risk of data breaches and other cyber incidents.
- Maintain business continuity by reducing downtime.
- Enhance customer trust and build strong customer relationships.
- Comply with industry-specific regulations and standards related to data protection, like HIPAA for healthcare and PCI DSS for payment card data security.
Types of Network Security Solutions
There are several types of network security protections that can be implemented to safeguard computer networks and data. Here are some of the most common types:
Network Access Control
Network access control restricts the access of unauthorized users to network resources, such as data files and applications. These include zero-trust network access solutions that give granular access at the user, group, or role level.
Firewalls
Network security firewalls monitor and filter incoming and outgoing traffic to prevent unauthorized access, attacks, data breach, and other threats. There are several types of firewalls, including packet filtering firewalls, stateful firewalls, and application firewalls.
Intrusion Detection and Prevention Systems(IDPS)
Intrusion prevention systems monitor network traffic to detect and prevent network intrusions and other security threats. They can be either network-based or host-based, including signature-based, anomaly-based, and heuristics-based detection methods.
Antivirus and Anti-Malware
Antivirus and anti-malware software detect, prevent, and remove malicious code from computers, mobile devices, and networks. This software can scan files and email attachments for viruses, trojans, worms, spyware, and other types of malware.
Virtual Private Network (VPN)
VPNs use encryption and tunnelling protocols to create secure connections between remote users and the network. This allows users to access network resources from remote locations while maintaining the web security and privacy of the data being transmitted.
Encryption
Encryption uses algorithms to transform data into an unreadable format that can only be decrypted with a key or password. This protects the user’s identity by hiding sensitive data in transit or at rest.
Application Security
Application security involves using secure coding practices, such as input validation and access control, to protect security vulnerabilities against attacks. This includes web application firewalls, vulnerability scanners, and code reviews.
Data Loss Prevention Solutions
Data loss prevention protects sensitive data from being lost, stolen, or exposed. These solutions work by monitoring, detecting, and preventing data breaches by enforcing policies, encrypting data, and providing access controls.
These network security protections can be implemented alone or in combination to provide comprehensive network security that safeguards sensitive data against a wide range of threats and attacks.
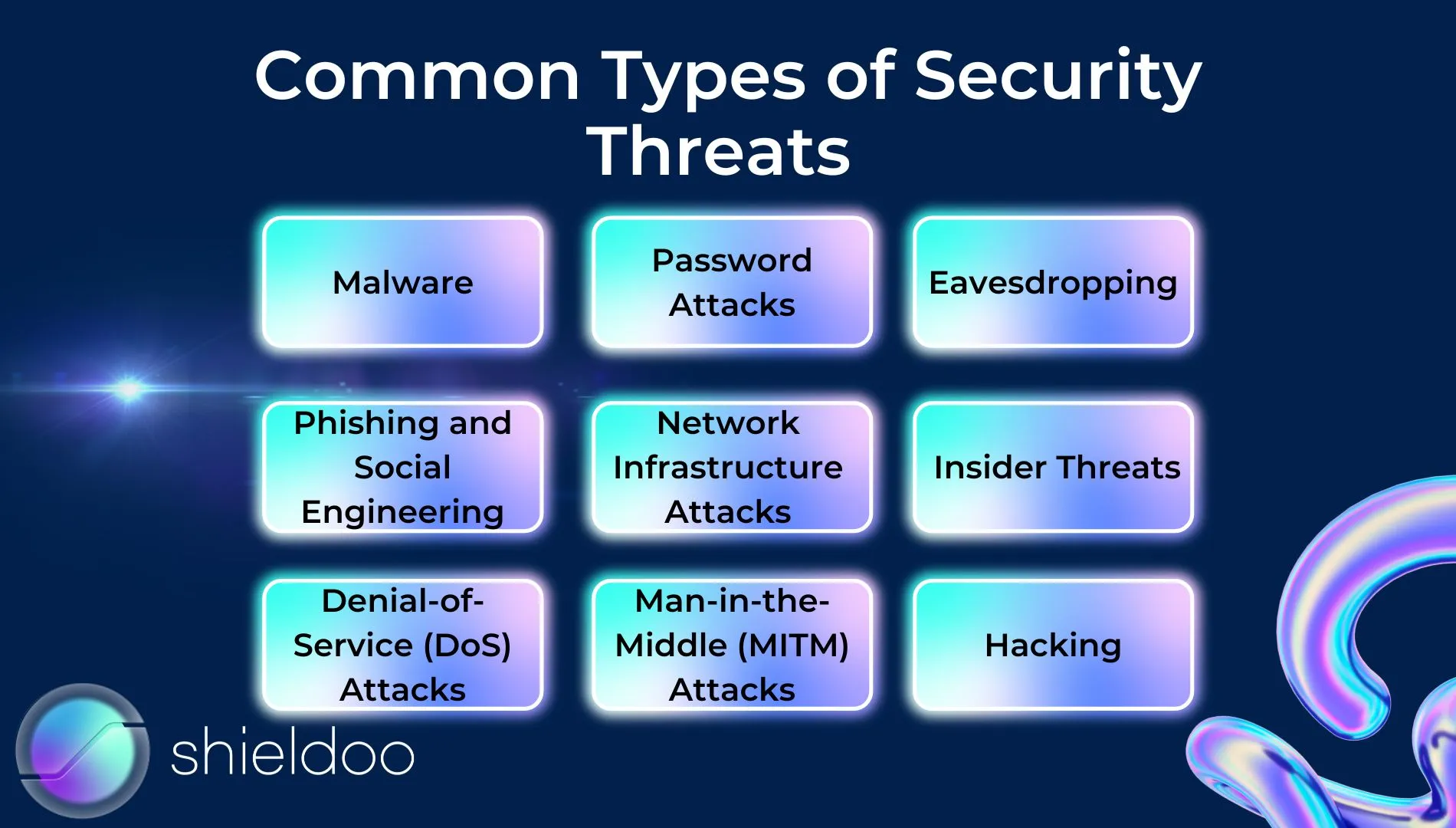
Common Types of Security Threats
Security threats pose significant risks to organizations and individuals. It's crucial to understand these threats and the appropriate network security controls to counter them.
Malware
Malware is malicious software that is designed to harm a computer or network. It can take many forms, including viruses, worms, Trojan horses, and ransomware. Network applications like antivirus and anti-malware software will protect users and cloud infrastructure from these external threats.
Phishing and Social Engineering
Phishing tricks users into divulging valuable data, such as passwords or credit card numbers. It uses social engineering, a technique that involves manipulating individuals to perform actions that are not in their best interest.
Corporate network security policies can prevent these types of cyberattacks by blocking access to known malicious websites and teaching employees the right user behaviour when handling company data.
Denial-of-Service (DoS) Attacks
A DoS attack is a type of cyberattack that seeks to overload a network or system with traffic in order to make it unavailable to users. This can be prevented by monitoring network traffic and blocking traffic that appears to be malicious or abnormal.
Password Attacks
Password attacks involve attempting to gain unauthorized access to a network or system by guessing or cracking passwords. Security policies like enforcing strong passwords, implementing multi-factor authentication, and monitoring for unusual login activity will protect data and deny access to potential attackers.
Network Infrastructure Attacks
Network infrastructure attacks target the underlying components of a company network, such as routers, switches, and firewalls. They can be prevented by implementing an intrusion prevention system to monitor network traffic and detect and block malicious activity.
Man-in-the-Middle (MITM) Attacks
MITM attacks happen when an attacker intercepts communication between two parties, and is able to eavesdrop on, alter, or inject new data into the communication. This can allow the attacker to steal valuable data. Network security methods, such as encryption and secure communications protocols, can help prevent MITM attacks.
Eavesdropping
Eavesdropping is the act of intercepting and monitoring communication between two parties without their knowledge or consent. Network security controls, such as encryption and secure communications protocols, can help prevent eavesdropping.
Insider Threats
Insider threats are security risks that originate from within an organization, such as an employee with access to sensitive information or systems. These threats can include intentional or unintentional actions, such as theft, data leakage, or sabotage. Access management systems detect and prevent insider threats.
Hacking
Hacking is the act of gaining unauthorized access to an organization’s network, often with the intent of stealing or manipulating data. Firewalls, IDPS, and access control systems can help prevent and detect hacking attempts.
High-Level Network Security With Shieldoo™️

Shieldoo™️ offers a range of benefits for online users seeking high-level security and privacy. With encrypted tunnelling, Shieldoo™️ protects your online activities and data from prying eyes.
Shieldoo's encryption is provided by reputable providers, ensuring that your data is protected by the most advanced encryption standards available. This means you’ll get a higher level of security than a classical remote access VPN.
Shieldoo's agent-based architecture offers more manageable and scalable protection than traditional VPNs, which often require complex network configurations. It uses end-to-end encryption, which reduces the risk of MITM attacks by encrypting data passing through Shieldoo™️ agents, making it unreadable to attackers even if they gain access to the network.
FAQs
How can I secure my network?
To secure your network, you can take several measures, including: implementing strong passwords, using encryption, regularly updating your software, installing firewalls and antivirus software, limiting physical access to your devices, backing up data regularly. Additionally, it's important to educate yourself and your employees about safe online practices and to monitor your network for any suspicious activity.
What is the best network security solution?
There is no single "best" network security solution, as the most effective solution will depend on the specific needs and requirements of the organization. Factors such as network complexity, type of data stored and transmitted, budget, and risk tolerance level affect your choice of network security solutions.The best security strategy involves multiple layers of security services like firewalls, IDPS, VPNs, security intrusion and event management (SIEM), managed security services, and endpoint protection software.
Why is network security important?
Network security protects your data and network against various cybersecurity threats, including hacking, malware, and phishing attacks. Without adequate network security, sensitive data and systems are vulnerable to unauthorized access and exploitation, which can lead to significant financial and reputational damage for individuals and organizations. Network security also helps to ensure compliance with relevant laws and regulations regarding data protection and can provide peace of mind for both network administrators and users. By implementing effective network security measures, organizations can reduce the risk of cyberattacks and safeguard their critical assets and data, ultimately leading to a more secure and reliable computing environment.





