Estimated read time: 9 minutes
As with observing a personal hygiene routine, precising cyber hygiene contributes to maintaining good health; it helps ensure the proper functioning of technology and preservation of data.
Cyber hygiene refers to a routine of precautionary measures and practices for protecting computing systems and sensitive data from cyberattacks and other security threats. It is a regular performance of security checks and pre-emptive diagnostics to prevent data corruption and exploitation of malicious entities.
Why is Cyber Hygiene Important?

As online activities increase, so do the number of cyber risks and vulnerabilities. Now more than ever, implementing cyber hygiene is important to mitigate data loss and security breaches.
Cyber hygiene helps organizations stay on top of their security protocols with regular performance checks and updates. Many a time, a missed software update will cause various issues in the workplace that will not only affect workflow but also put sensitive data at risk of cyber threats.
Software and data aren’t the only concerns of cyber hygiene. The functionality of hardware enables IT security teams to implement efficient security measures. Devices must be diagnosed with underlying processing issues or ransomware mimicking other IT-approved programs.
Good cyber hygiene enables organizations to maintain system health, reinforce security posture, and perform at optimal levels. Robust online security empowers organizations to scale business operations on the Internet.
What are the Benefits of Cyber Hygiene?
What good is cyber hygiene? Just like how daily brushing and flossing of one’s teeth prevent the formation of cavities, checking up on your computer system’s health keeps away cyber threats and performance issues.
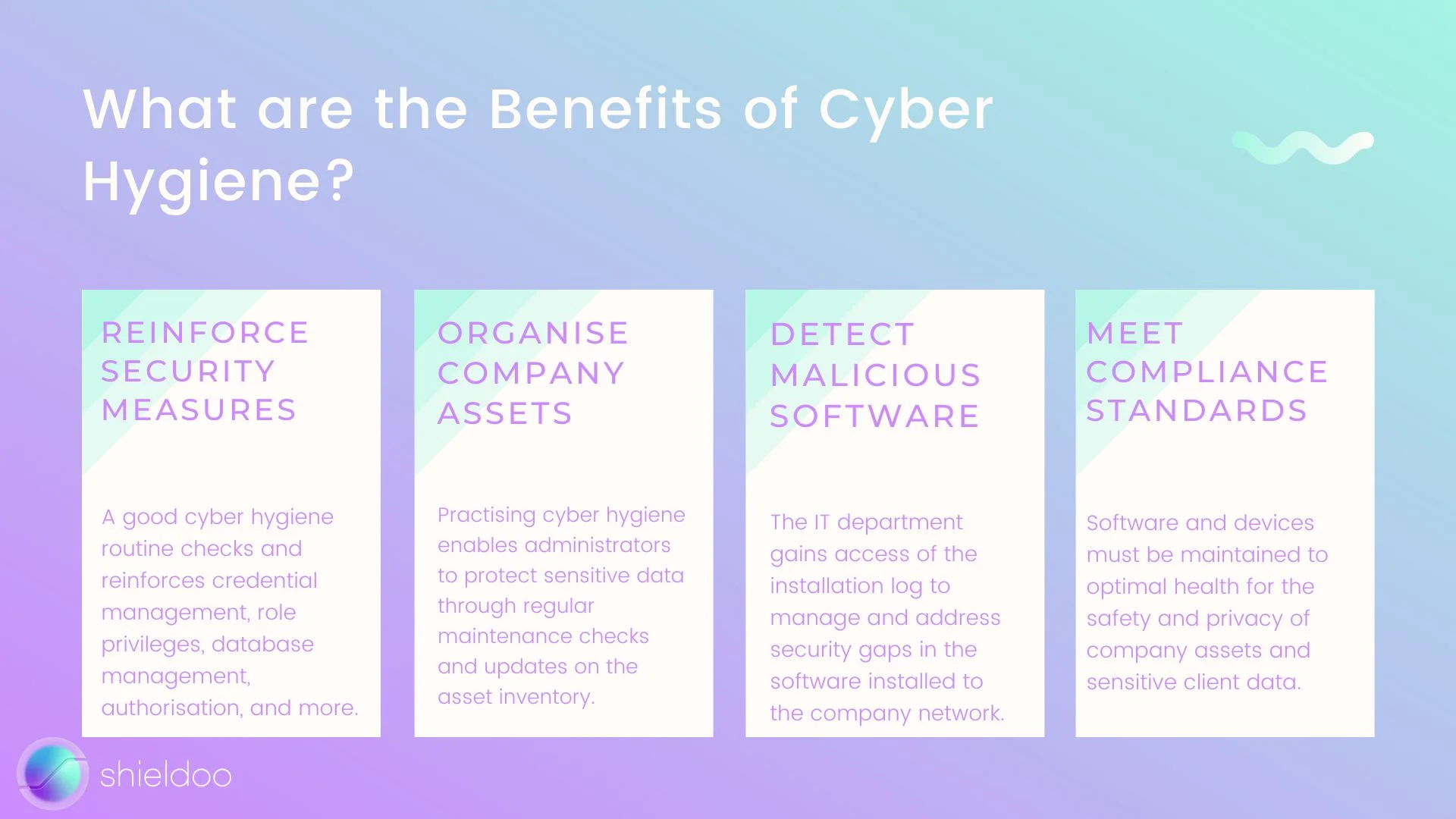
Reinforce Security Measures
Cyber hygiene ensures that the security infrastructure of an individual or organization's computer system is running efficiently. As cybercriminals grow more cunning, it is a high priority for companies to review their security measures regularly. A good cyber hygiene routine checks and reinforces credential management, role privileges, database management, authorization, and more.
Organize Company Assets
A disorganized asset library is vulnerable to malicious attacks and internal breaches. It can be challenging for large organizations to manually locate and segregate assets. Precising cyber hygiene enables administrators to protect sensitive data through regular maintenance checks and updates on the asset inventory. Monitoring each asset prevents vulnerabilities and threats from further contaminating sensitive data.
Detect Malicious Software
Remote and hybrid work setups urged business users to incorporate several third-party software in delivering daily tasks. While harmless on the surface, these services do not have the approval of the IT security team nor meet the company compliance requests. Cyber hygiene practices keep malicious software from compromising computer systems and data networks. The IT department gains access of the installation log to manage and address security gaps in the software installed to the company network.
Meet Compliance Standards
Cyber hygiene enables the IT security team to ensure the organization's technology stack is aligned with governance and compliance requirements. Software and devices must be maintained to optimal health for the safety and privacy of company assets and sensitive client data.
What are the Risks of Poor Cyber Hygiene?
Just like how poor personal hygiene may lead to a range of health issues, poor cyber hygiene can compromise the security posture of business networks. Poor cyber hygiene gives rise to security risks and critical vulnerabilities.
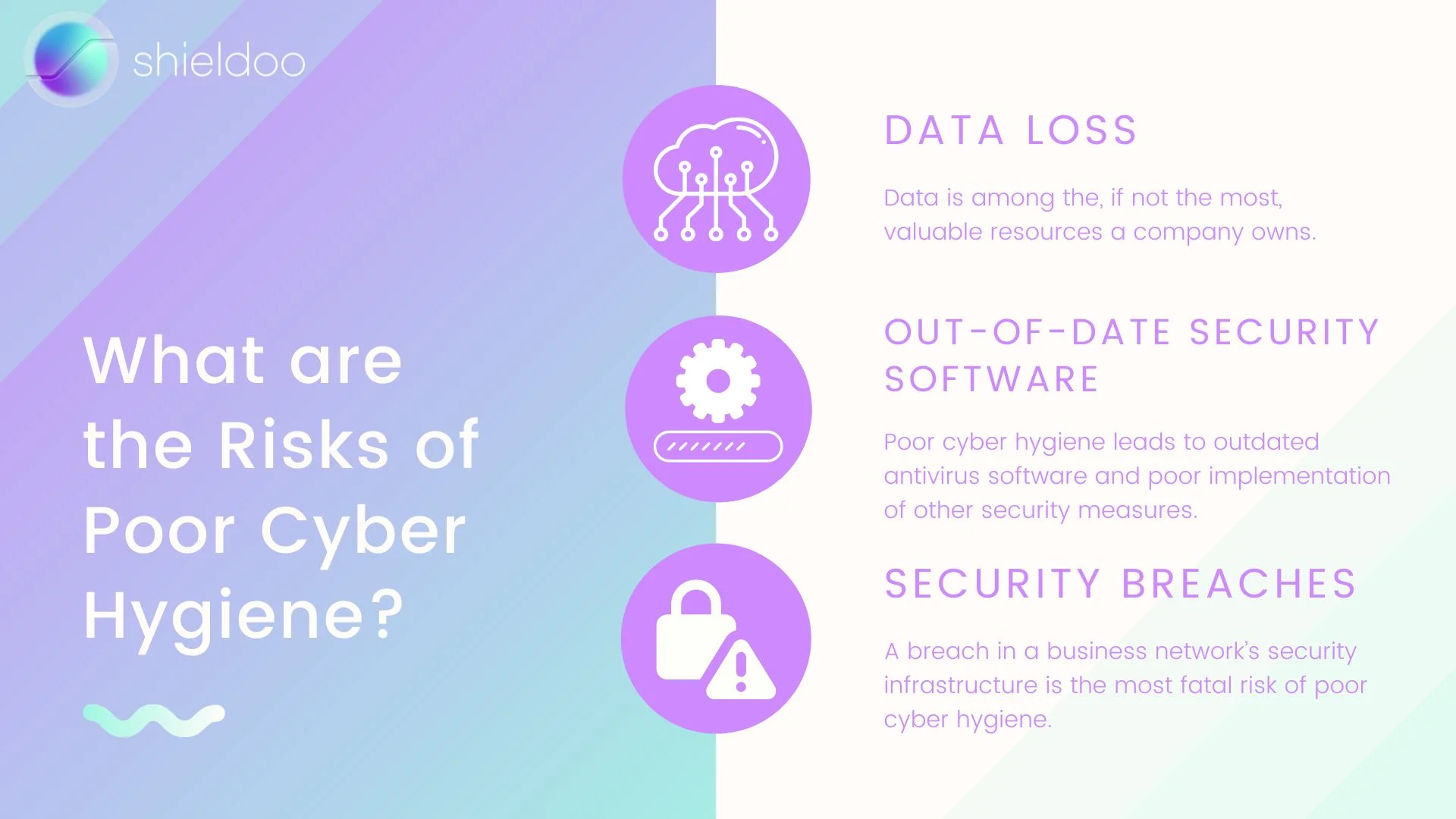
Data Loss
Data is among the, if not the most, valuable resources a company owns. Critical data, such as client information, are irreplaceable should online databases be corrupted or local data repositories aren’t backed up. Irregular backups, hardware failure, and poor data management can cost organizations millions of dollars in data loss.
Poor cyber hygiene is vulnerable to phishing attacks, which cost $4.91 million on average. Personal credentials are the most common targets for hackers to infiltrate networks and compromise data.
Out-of-date Security Software
Poor cyber hygiene leads to outdated antivirus software and poor implementation of other security measures. Security breaches commonly occur due to organizations running older versions of security software. Security patches are regularly released to address known issues and bugs that compromise the security and privacy of networks.
Without a regular maintenance check on software and security, companies fall short of preventing cybercriminals from exploiting software vulnerabilities to compromise networks and data repositories.
Security Breaches
A breach in a business network’s security infrastructure is the most fatal risk of poor cyber hygiene. 83% of organizations suffer the damages of data breaches due to poor security protocols. The 2022 Cost of a Data Breach report from IBM shows that the global total spend of a data breach costs $4.35 million.
Without a good cyber hygiene routine, an organization experiences massive losses in data integrity, finances, and most importantly, customer trust.
What are the Best Cyber Hygiene Practices?
Maintaining cyber hygiene is vital to the overall functioning and security of a business network. It involves running diagnostic checks and updating software to their latest versions, from operating systems and antivirus programs, all the way to web browsers.
Stay vigilant with good cyber hygiene practices such as the following:
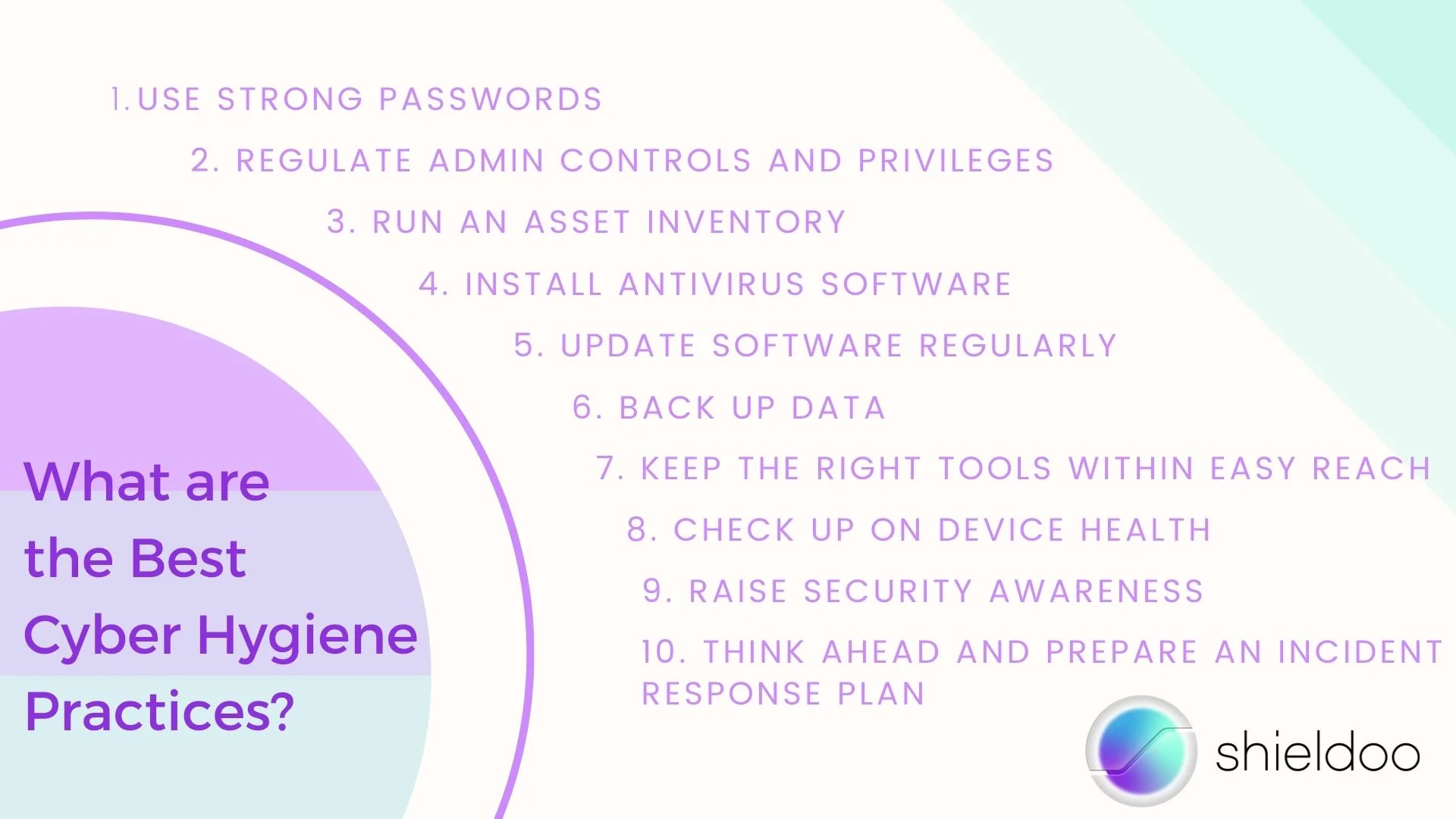
Use Strong Passwords
Strong and complex passwords are a must to deflect security threats. A strong password is around 10-15 characters long, with a combination of uppercase and lowercase letters, special characters, and numbers. Updating passwords on a regular basis also prevents data breaches by insider acts.
Setting up multi-factor authentication (MFA) is an excellent security measure to reinforce a user’s identity for every new login session. Users are required to verify their identity by security code, fingerprint, or face recognition.
Regulate Admin Controls and Privileges
Roles in a computer system are assigned according to the minimum access a user requires to accomplish their tasks. Implementing layered privilege access limits a user’s activity on the network and restricts access to more critical resources and applications to administrative roles.
Run an Asset Inventory
Should hackers get pat your security systems, it is important to know which assets were stolen or compromised. An asset inventory helps keep track of the value, location, user rights, and health status of company assets. With an asset inventory, organizations can minimize security incidents such as misplaced data. Assess the level of protection each asset requires to apply the appropriate security measure.
Install Antivirus Software
Basic cyber hygiene includes installing antivirus software to deflect phishing attacks, trojan horses, and other malicious software from infiltrating the company network. In fact, many security incidents can be prevented with a reliable antivirus program. Invest in reliable antivirus software that can protect user traffic on the local network and on the cloud.
Update Software Regularly
New patch releases address known issues and vulnerabilities that your operating systems may have been experiencing. Make sure to update applications to seal security gaps and defend the network from cybercriminals exploiting known vulnerabilities.
Back Up Data
Keep multiple backups of data and stay a few steps ahead of cybercriminals. Cloud storage and external hard drives are great options to keep copies of data backup. When you modify system files or incorporate new software, chances are high for users to risk losing personal data. Backing up data enables you to cross-check discrepancies in existing files and restore previous file versions whenever necessary. Verify the success of every backup to ensure all information are readable. Check the health of hard drives as well; corrupted hardware risks data loss.
Keep the Right Tools within Easy Reach
Should the need to eliminate data rise, data-wiping software helps to permanently erase all traces of compromised files from hard drives. A network firewall is another staple of cybersecurity; with a network firewall, unauthorized users cannot access email, web, and other online servers to gain entry to your business network.
Check Up on Device Health
In line with checking up on external hard drives, it is a good cyber hygiene practice to monitor device health. Computers and mobile devices connected to the network are vulnerable to malicious attacks. Run regular security scans on connected devices to mitigate the spread of ransomware and secure sensitive data from malicious individuals.
Raise Security Awareness
A good cyber hygiene routine involves every user on the network. Maintaining system health and online security is a team effort; employees have to observe these security measures across company-issued and personal devices to ensure no data will be accidentally leaked. Provide employees with a cyber hygiene checklist to serve as a daily reminder to protect and secure their data and activities on the Internet.
Think Ahead and Prepare an Incident Response Plan
No organization is immune to security threats; thus, it is best to incorporate an incident response plan in your security protocols to mitigate damages. Data breaches take no more than a few hours for hackers to wipe out critical data from your network. Implement a fast-action incident response plan to quickly cut off the hacker’s data exfiltration.
The IT security team can run simulation tests of data breaches to determine the speed and effectiveness of the incident response plan.
The Cyber Hygiene Checklist to Maintain System Health and Online Security
Cyber hygiene can’t be accomplished in a fortnight—it is a practice that business users must observe at all times to protect key information and activity on the Internet.
Stay on top of your cyber hygiene routine with this handy checklist:
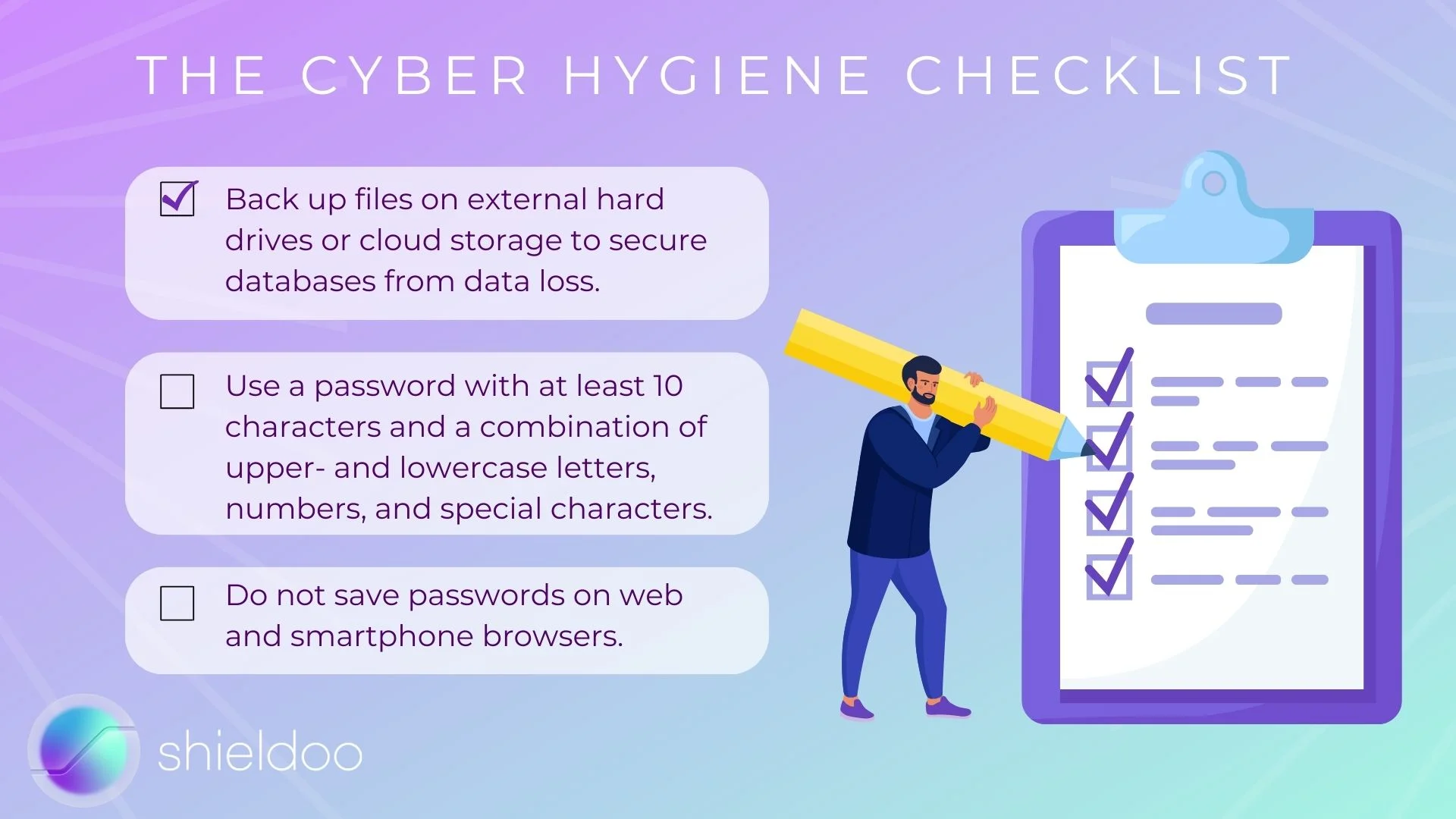
- Backup files on external hard drives or cloud storage to secure databases from data loss.
- Use a password with at least 10 characters and a combination of upper- and lowercase letters, numbers, and special characters.
- Do not save passwords on web and smartphone browsers.
- Use a password manager to keep track of user credentials.
- Implement multi-factor authentication to add an extra layer of security during user login attempts.
- Enable network firewalls, VPN, and other IT security solutions to protect user activity on the Internet.
- Update operating systems, firmware, web browsers, and other programs to the latest versions to apply the latest security patches.
- Use reliable antivirus software to address computer virus attacks and other malicious software corrupting files and programs.
- Ignore suspicious email, website links, and text messages to mitigate phishing incidents.
Optimize Business Performance and Mitigate Security Threats with Cyber Hygiene

In essence, cyber hygiene is a security-centric routine that protects critical data and optimizes the performance of hardware and software. The collective efforts of users in a business network strengthen security measures and mitigate incidents of cyberattacks. Incorporating IT security solutions such as zero trust network access (ZTNA) provided by Shieldoo™️ secure network (mesh) technology will enable organizations to deflect malicious attacks and scale online operations seamlessly.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What does good cyber hygiene look like?
Good cyber hygiene refers to the regular practice of security measures, from virus scans and program updates to managing files and cleaning up hard drives. It requires the use of reliable tools to enable reliable security against cyberattacks and efficient data management. For instance, an organisation with a good cyber hygiene performs weekly virus scans with antivirus software that can detect, isolate, and terminate malicious software.
Who is responsible for maintaining cyber hygiene?
Cyber hygiene is a responsibility shared by business users across departments and management levels. It requires the cooperation of employees in observing simple yet effective practices in protecting data privacy and user activity, such as creating strong passwords or avoiding public Wi-Fi networks.
What is the top priority of cyber hygiene?
The main goal of practicing cyber hygiene is to reinforce the security infrastructure of networks and mitigate ransomware incidents. With hackers and other malicious entities learning elusive ways in infiltrating private networks, organisations must implement a competent cyber hygiene policy to detect the first signs of a cyber threat and execute the appropriate incident response.





