Estimated read time: 5 minutes
What is single sign-on?
Single sign-on (SSO) is an authentication solution allowing users to use one set of login credentials to access multiple applications or websites. SSO is an effective method for companies to strengthen their security measures. As for the end-users, SSOP saves them from password fatigue— the burden of recalling and managing passwords for different accounts.
Companies adopt SSO for efficient access management. Enhancing the security for a single set of credentials with multi-factor authentication is more manageable than running through multiple entry attempts of a single user.
On the other hand, SSO grants end-users quick and easy access to several platforms with just a set of credentials. Single sign-on eliminates the stress of dealing with multiple passwords, boosting user experience and ease of adding another device to make use of the credentials.
How does SSO work?

SSO verifies the identity of the user and/or device attempting to log in to a platform. With SSO, networks can determine the appropriate access level to grant to users in order to fulfill their tasks or accomplish their goals, without exposing more critical or sensitive data.
For SSO to work effectively, trust must be set up between the service provider (SP) and the identity provider (IdP). A service provider such as Instagram, for instance, would redirect a user to authenticate their identity with Facebook, the identity provider. After confirming the user’s identity and intent on Facebook, the user can now access their Instagram account.
Trust between a service provider and the identity provider is crucial to establishing that the request for access is coming from a valid and reliable webpage. While the two providers are exchanging information, bits of said information are encrypted into authentication tokens.
Basic login flow
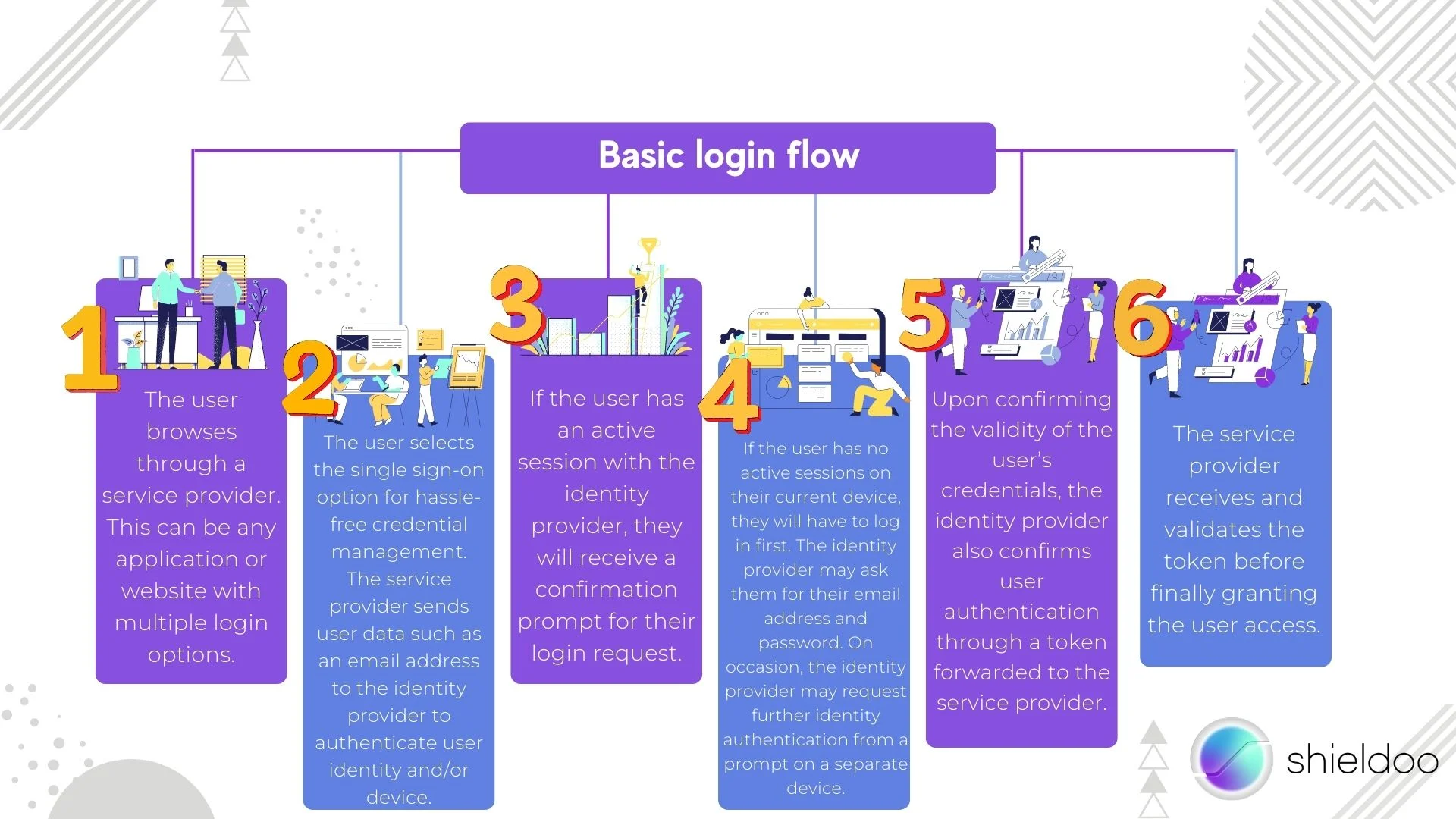
A typical SSO login follows such a flow:
- The user browses through a service provider. This can be any application or website with multiple login options.
- The user selects the single sign-on option for hassle-free credential management. The service provider sends user data such as an email address to the identity provider to authenticate user identity and/or device.
- If the user has an active session with the identity provider, they will receive a confirmation prompt for their login request.
- If the user has no active sessions on their current device, they will have to log in first. The identity provider may ask them for their email address and password. On occasion, the identity provider may request further identity authentication from a prompt on a separate device.
- Upon confirming the validity of the user’s credentials, the identity provider also confirms user authentication through a token forwarded to the service provider.
- The service provider receives and validates the token before finally granting the user access.
What is an SSO Authentication Token?

The SSO process requires information to be passed between providers to validate user authentication. Bits and pieces of data are collected into an SSO authentication token. Digital information stored in authentication tokens may contain a user’s email address, username, and password. Service and identity providers exchange certificates to sign the verification that the token is provided by a trustworthy source.
The Security Benefits of Single Sign-on
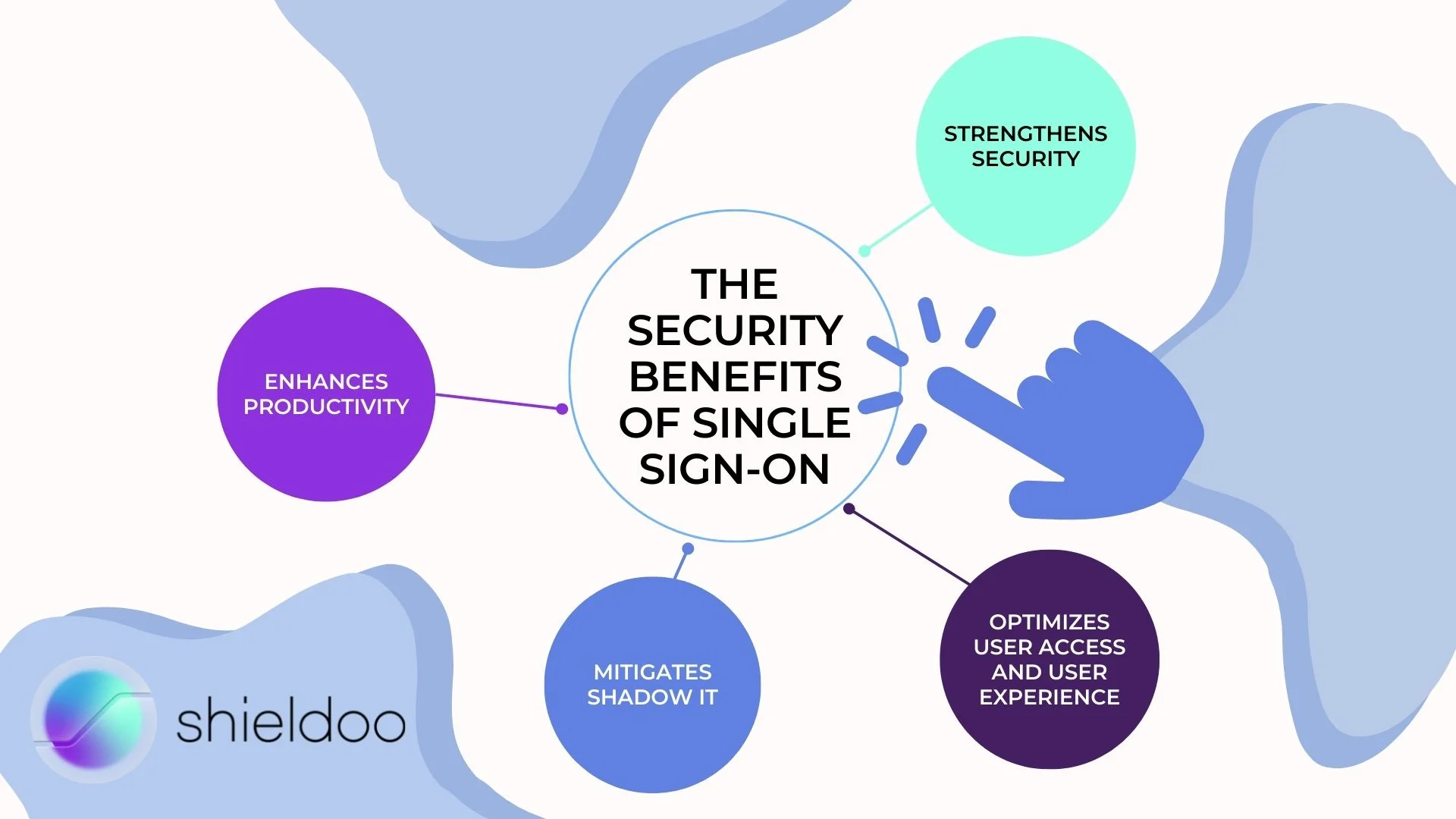
From reducing login attempts to managing stronger passwords, single sign-on offers a handful of benefits for companies and end-users alike.
Enhances productivity
With just one set of user credentials, access is authenticated across several applications and websites. Single sign-on significantly cuts down the time wasted recalling usernames or resetting passwords.
Logging in between sites is a smoother experience with SSO. The IT department is less likely to be flooded with support tickets for account recovery or password reset.
Strengthens security
Users are granted the opportunity to come up with a strong and unique password to use for all their login attempts with single sign-on. With only one password to remember at all times, users will have no problem creating a challenging password to fortify their account from security threats.
Today, it is common practice for companies to incorporate single sign-on with multi-factor authentication for an extra security layer. Multi-factor authentication (MFA) for further verification of user identities. A common method is requesting to input a security code sent to another mobile device or email address.
Optimizes user access and user experience
Ease of access and phenomenal user experience are welcomed benefits of adopting an SSO system. As society becomes more dependent on cloud services, multiple logins can occur in just a day. Single sign-on saves users from the hassle of recalling a dozen or so credentials, extinguishing the stress that comes with forgotten passwords and incorrect usernames.
Mitigates shadow IT
Implementing an SSO system cuts back on the issues that may arise with the prevalent use of shadow IT. The IT department can elevate security measures through single sign-on support limited to approved applications. With shadow IT at bay, the risk of data breaches and non-compliance to IT standards is significantly lessened.
SSO Authentication Specifications and Protocols
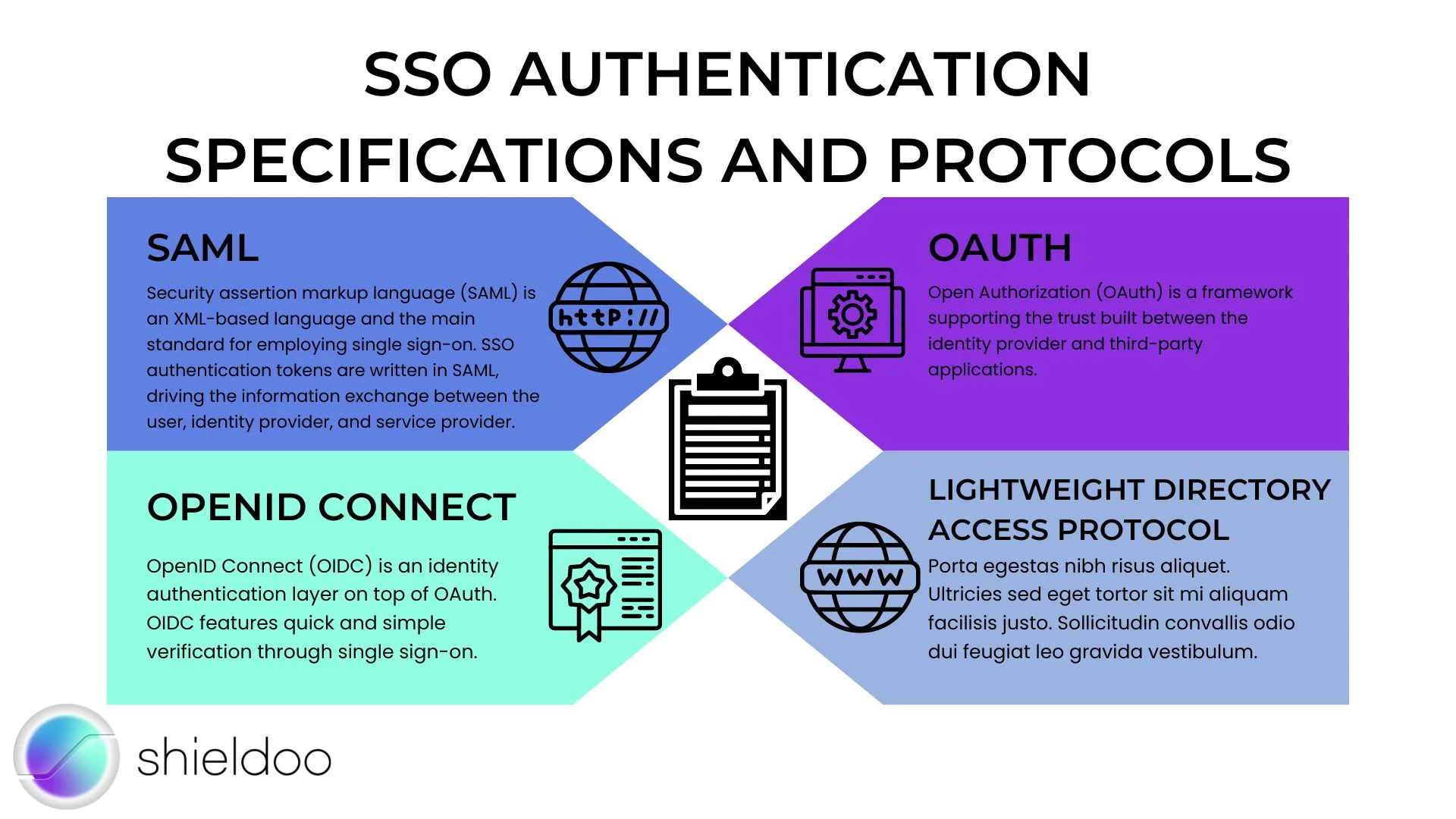
Single sign-on (SSO) is just one feature of Federated Identity Management (FIM). FIM is a collection of standards and specifications to be met in order for providers to exchange information on user identities. SSO employs several standards to support secure and efficient management of tokens, organization systems, and more.
SAML
Security assertion markup language (SAML) is an XML-based language and the main standard for employing single sign-on. SSO authentication tokens are written in SAML, driving the information exchange between the user, identity provider, and service provider.
OAuth
Open Authorization (OAuth) is a framework supporting the trust built between the identity provider and third-party applications.
OpenID Connect
OpenID Connect (OIDC) is an identity authentication layer on top of OAuth. OIDC features quick and simple verification through single sign-on.
Lightweight Directory Access Protocol
The Lightweight Directory Access Protocol (LDAP) is used for organizing directory information distributed over a network. It defines and controls access to directories such as an active directory (AD). Rather than verifying user identity or granting user access, the LDAP exercises central authority over the management of information stored in a system.
Shieldoo™️ and Single Sign-On
As a next-gen innovation for secure and private networks up on the cloud, Shieldoo™️ comes with state-of-the-art features for secure user access wherever you may be. Shieldoo™️ implements single sign-on for quick and easy access to the software’s functions. Simply use your Google or Microsoft account to log in, and you’re good to go. Enhance security by enabling two-factor authentication.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What is SSO (Single Sign-On)?
Single sign-on (SSO) is an authentication solution that enables users to gain access to multiple applications and websites with a single set of login credentials.
Is SSO safe to use?
The rise of cloud computing services has led to the expansion of SSO providers on the Internet. Single sign-on and secure access are granted to companies and end-users as a SaaS solution.
Why use SSO?
Single sign-on (SSO) limits the point of entry to one set of login credentials. Despite logging in on different applications, users are less exposed to cyberattacks. A single set of powerful credentials enhances the security, productivity, and conversion rates of enterprises.
How important is an authentication token?
SSO solutions require an authentication token in order for the user to gain access to a particular website or application. Without the token, user identity cannot be verified between the service provider and identity provider.
Does SSO grant secure access?
Single sign-on is just one component of a company’s complex network of security solutions. An SSO solution does not grant secure access on its own, but rather through a culmination of efforts from the different security measures implemented.
Is SSO a Software as a Service (SaaS)?
The rise of cloud computing services has led to the expansion of SSO providers on the Internet. Single sign-on and secure access are granted to companies and end-users as a SaaS solution. Shieldoo™️ integrates SSO solutions to define user identity and role inside a network.





