Estimated read time: 7 minutes
Authentication and authorization are two terms regularly mentioned in the discourse of system security and identity access management. Often used interchangeably, these security processes perform significant roles in safeguarding systems and confidential data.
Simply put, authentication verifies user identity, whereas authorization determines user permission to access resources. These two processes work together in managing access control and user privileges within the system.
How Do They Differ: Authentication vs. Authorization
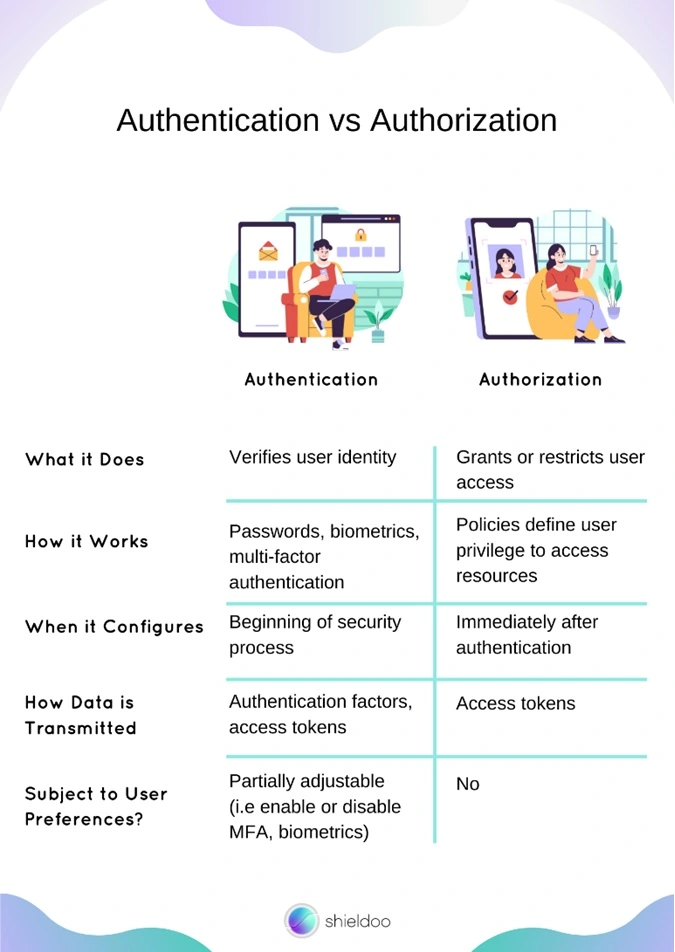
Authentication and authorization tend to be mistaken as interchangeable terms in system security. However, the two are entirely separate steps of a security process. Before we dig deeper into how authentication and authorization work and maintain the security of computing systems, let us take a look below at the comparison chart of their differences.
What Is Authentication?
Authentication verifies the identity of a user. It is the first step of a thorough security process that users go through to access files and applications on a system.
The authentication process begins with a thorough crosscheck of user credentials provided by the user and those recorded in the system’s user credential log. A successful authentication shows a positive match, granting access to the system.
Commonly Used Authentication Factors
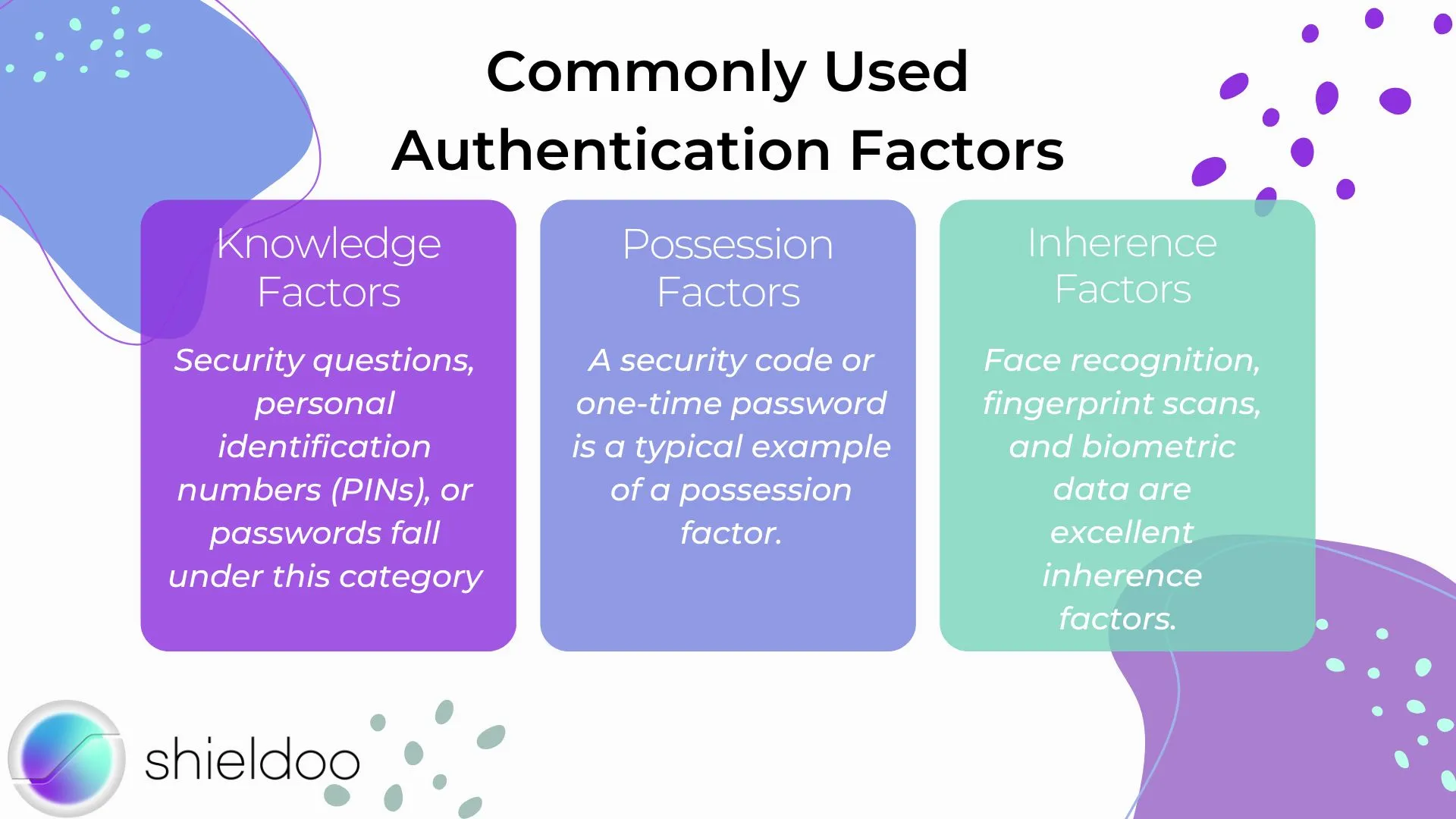
Authentication systems use factors to authenticate the identity of a user. Authentication factors are pieces of evidence that prove the user is who they claim to be.
Knowledge Factors
Knowledge factors refer to any piece of information that is “something the user knows”. Security questions, personal identification numbers (PINs), or passwords fall under this category. Wrong entries restrict or deny access to the system.
Possession Factors
Possession factors prompt the user to provide evidence that is within their possession. A possession factor is “something the user has” and is retrieved from a previously recognized device. A security code or one-time password is a typical example of a possession factor.
Inherence Factors
Inherence factors authenticate user identity according to their unique characteristics. They correspond to the authentication prompt: “something the user is”. Face recognition, fingerprint scans, and biometric data are excellent inherence factors.
Authentication Methods
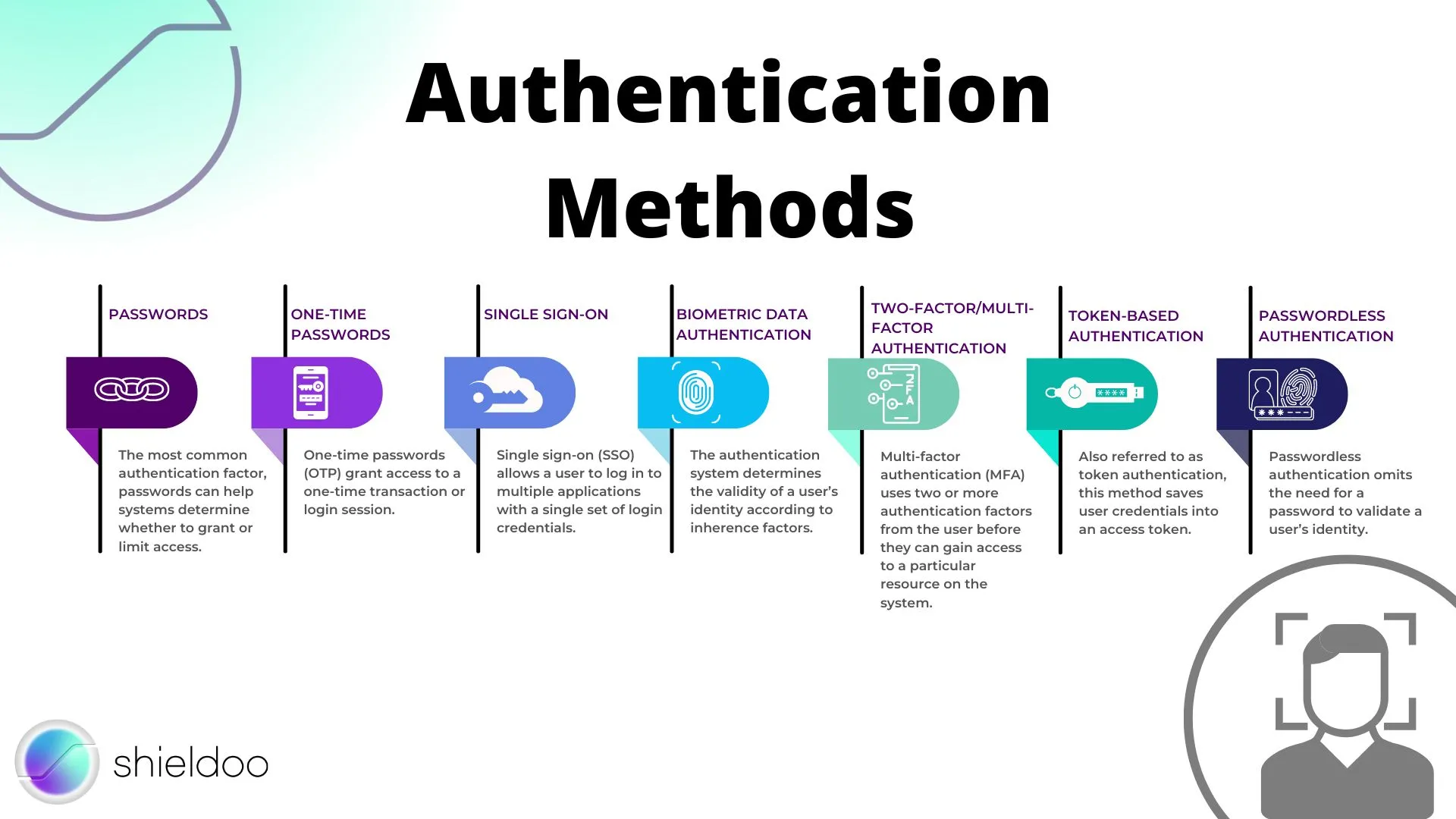
Authentication systems can combine more than two authentication factors to increase the level of security. Let us take a look at the different factors and methodologies authentication systems adopt:
Passwords
The most common authentication factor, passwords can help systems determine whether to grant or limit access. However, passwords are the least secure, as they are vulnerable to external attacks.
One-Time Passwords
One-time passwords (OTP) grant access to a one-time transaction or login session. An OTP is a computer-generated string of characters that the authentication system may deliver to the user via text message, email, or an access token.
Single Sign-On
Single sign-on (SSO) allows a user to log in to multiple applications with a single set of login credentials. An identity provider like Google or an Active Directory in workplace systems authenticate the login attempts of a user across websites, improving security and saving time to recall multiple passwords.
Biometric Data Authentication
The authentication system determines the validity of a user’s identity according to inherence factors. It runs face recognition, fingerprint scans, voice recognition, compares and contrasts the biometric data provided by the user with those recorded in the database.
Two-Factor/Multi-Factor Authentication
Multi-factor authentication (MFA) uses two or more authentication factors from the user before they can gain access to a particular resource on the system. MFA is a popular authentication methodology these days, as it increases security, minimizing the risk of internal data breaches due to malicious logins.
Token-Based Authentication
Also referred to as token authentication, this method saves user credentials into an access token. Third-party services and websites refer to access tokens to confirm the user’s identity. It follows the principle of MFA; the user can login to multiple applications or sites with only an access token for quick and easy identity verification.
Passwordless Authentication
Passwordless authentication omits the need for a password to validate a user’s identity. Instead, it uses an inherence factor, a possession factor, or a combination of both. These include one-time passwords, magic links, biometric data, and push notifications.
What Is Authorization?
Following authentication, authorization determines the level of access a user is entitled to. Authorized users gain access to the resource or command prompt they require from the system.
The system recognizes an authenticated user, granting them their request to access a file or execute an action. Authorization is also used interchangeably with client privilege or access control.
Authorization Permissions
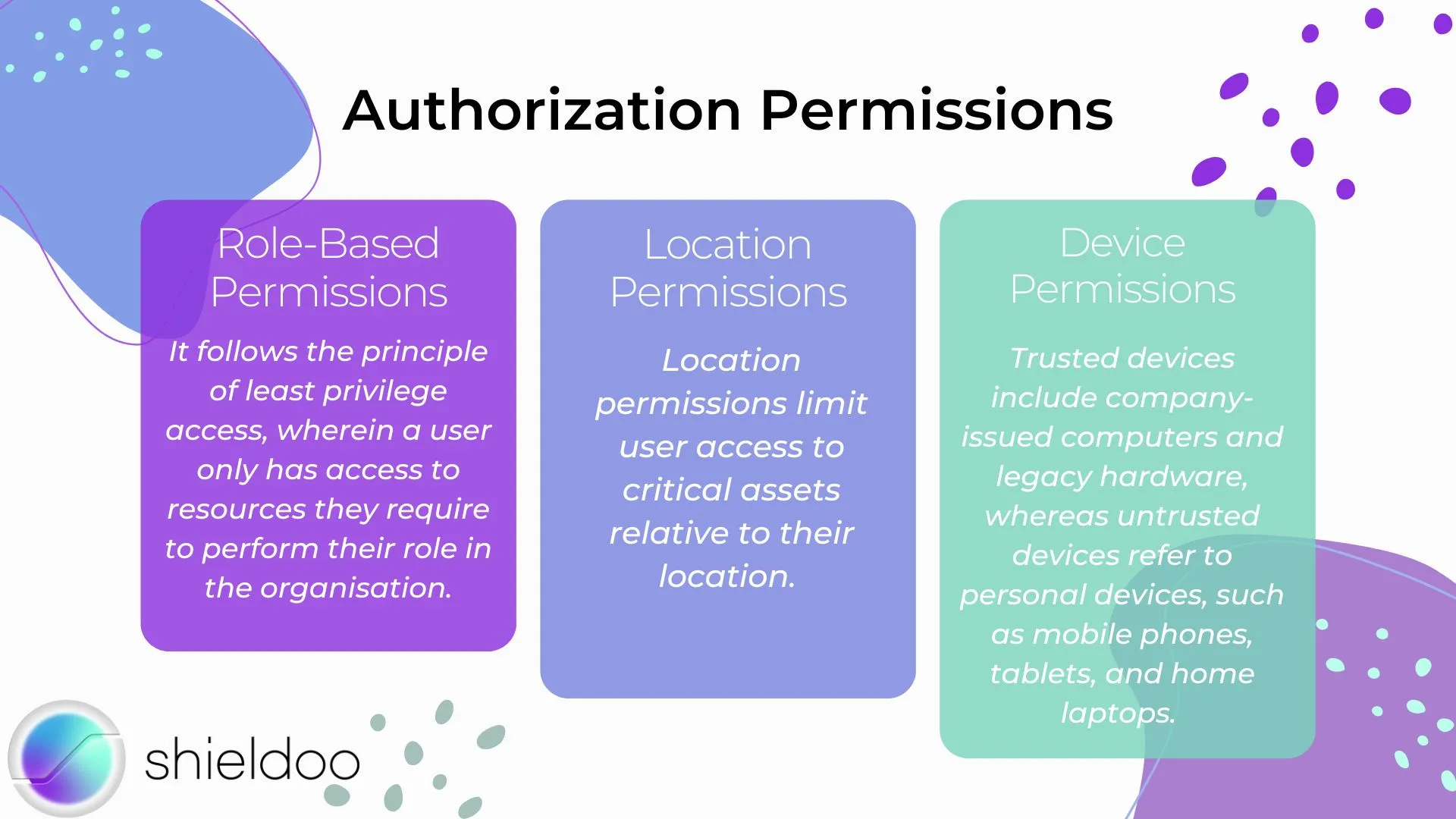
The authorization process involves granting the authenticated user permission to retrieve resources or execute actions within the scope of their role. Assigned roles define a user’s privilege or influence within the computing system.
Role-Based Permissions
Role-based permissions allow users with a common role in the business to access a specific set of resources. It follows the principle of least privilege access, wherein a user only has access to resources they require to perform their role in the organization.
Location Permissions
Location permissions limit user access to critical assets relative to their location. The vulnerability of remote access to prying eyes prompts authorization systems to restrict access to the more sensitive data.
Device Permissions
Device permissions differ according to the level of trust an authorization system shares with a device. Trusted devices include company-issued computers and legacy hardware, whereas untrusted devices refer to personal devices, such as mobile phones, tablets, and home laptops. Device health and security are fundamental in granting an appropriate set of device permissions.
Authorization Techniques
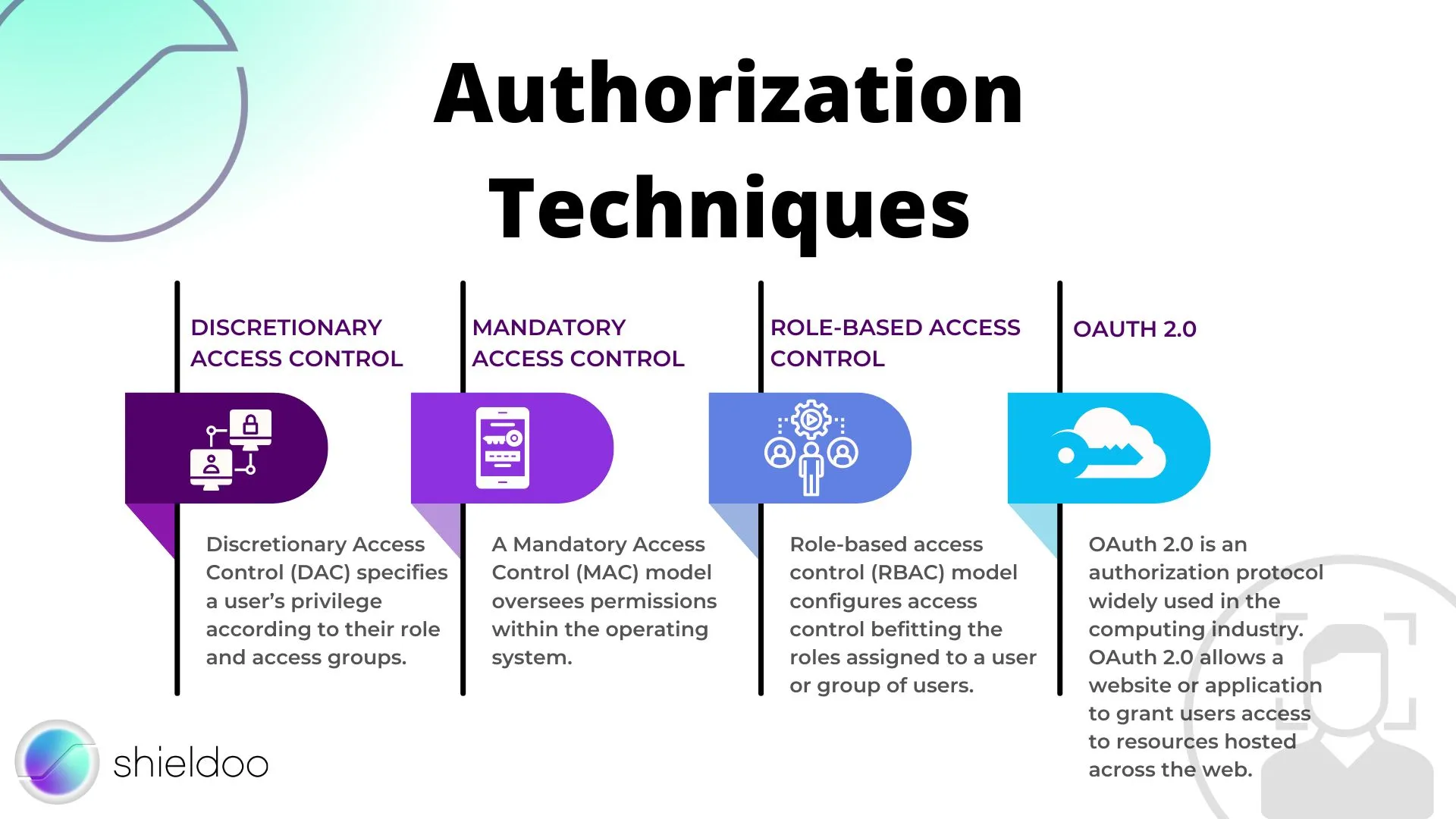
Authorization systems grant permissions that are entitled to users through a varied range of protocols. Below are the commonly used techniques to deploy authorization systems:
Discretionary Access Control
Discretionary Access Control (DAC) specifies a user’s privilege according to their role and access groups. With a DAC model, all objects on the system are accessible to a specific user or user group.
Mandatory Access Control
A Mandatory Access Control (MAC) model oversees permissions within the operating system. Users eligible to access operating system files and processes can modify or execute changes within the scope of permissions granted by the MAC model.
Role-Based Access Control
Role-based access control (RBAC) model configures access control befitting the roles assigned to a user or group of users. Objects within the system are made accessible to users who meet authorization requirements.
OAuth 2.0
OAuth 2.0 is an authorization protocol widely used in the computing industry. OAuth 2.0 allows a website or application to grant users access to resources hosted across the web. A user or client provides their access token. After the client is successfully authenticated, the authorization server receives and delivers the access request retrieved from the resource server.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
Is login authentication or authorization?
User login is part of the authentication process. A user enters their login credentials, which the authentication system requires to validate the user’s identity.
What are the three types of authentication factors?
A user can authenticate their identity by providing evidence, called authentication factors. Authentication factors come in three types: knowledge (passwords, security questions, one-time passwords), possession (security codes from a trusted device), and inherence (face recognition, voice recognition, fingerprint scans) factors.
Which comes first, authentication or authorization?
Authentication is the first step in the security process and comes before authorization. Authorization takes place upon successful user authentication.





