Estimated read time: 4 minutes

In this article we would like to share our experience with running servers in the internet zone and why servers operating without communication restrictions are easy targets for attackers. Let's show it on a practical example, and we will see how attackers will take care of our server.
The main idea behind our experiment is to create a standard server somewhere in the public cloud and start there few services simulating common databases, web servers or remote access solutions.
We often read articles about hacked systems and how the Internet is dangerous, but what happens in real life? How our server will survive in the outside world? Is it true that hackers are trying to attack even if we are a small server somewhere in the corner of the Internet? There is also a question what happens if someone uses a password like "test" or "password" for a "root" user?
Consider the Following Scenario:
I installed a Linux operating system and emulation of an HTTP server, SSH server, VNC server, MySQL database and Postgres databases on our machine. This machine is run in Hetzner Cloud Console (personally, Hetzner is a very cool public cloud provider for simple infrastructure workloads). The emulator shows our server connect and login attempts with detailed information about the attacker's IP address and activities.
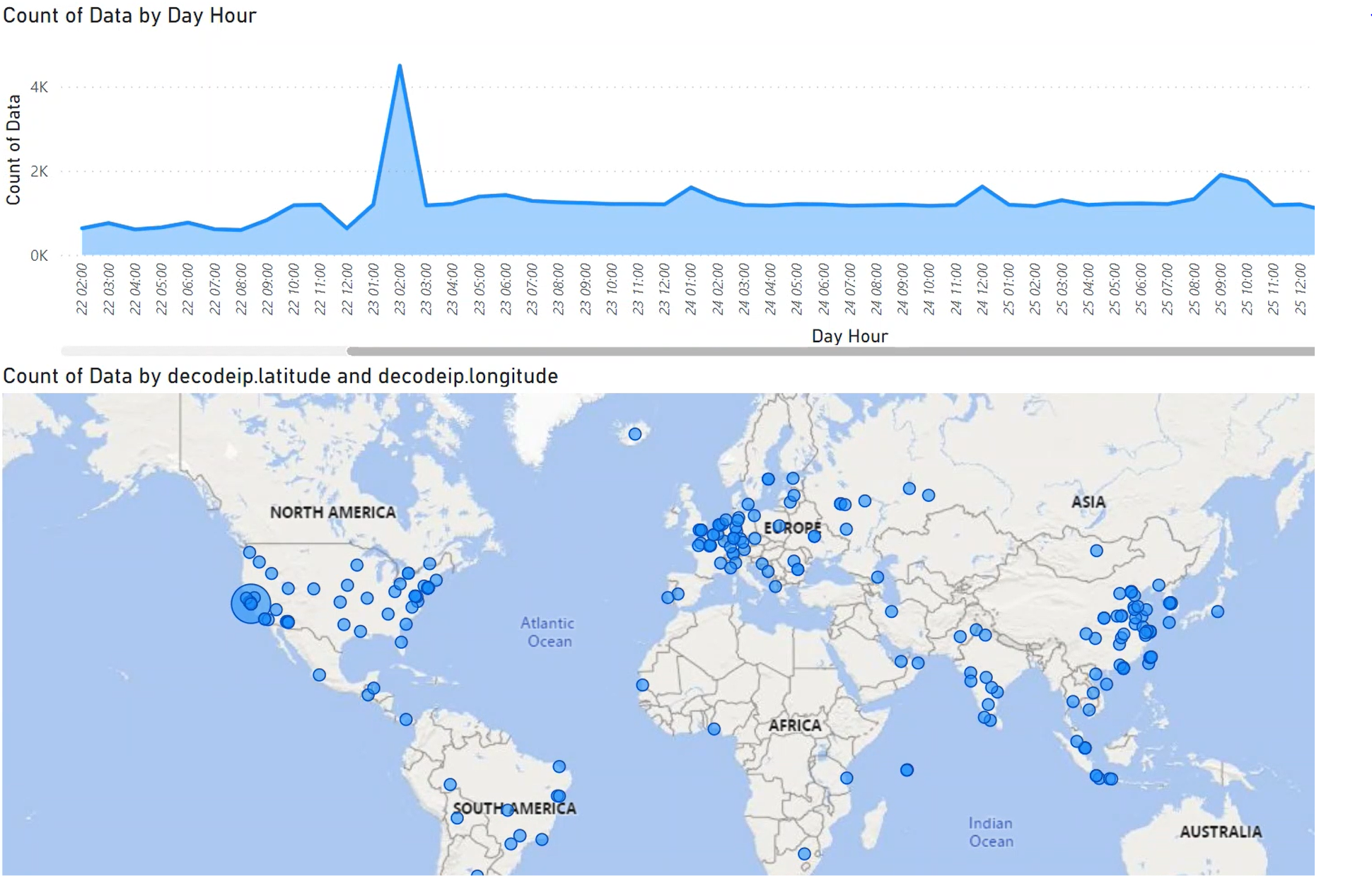
From statistics stored in our server, we can learn interesting things:
- first connection attempt to our server we can see just after 3 minutes (!), an attacker tries to connect to SSH service
- after 20minutes, we can see there many connection attempts to HTTP, MYSQL and POSTGRES services
- there is a connection rate of 2500 connections per hour from attacker's bots trying to login into our services
- it's clear that attackers are using password dictionaries for attack
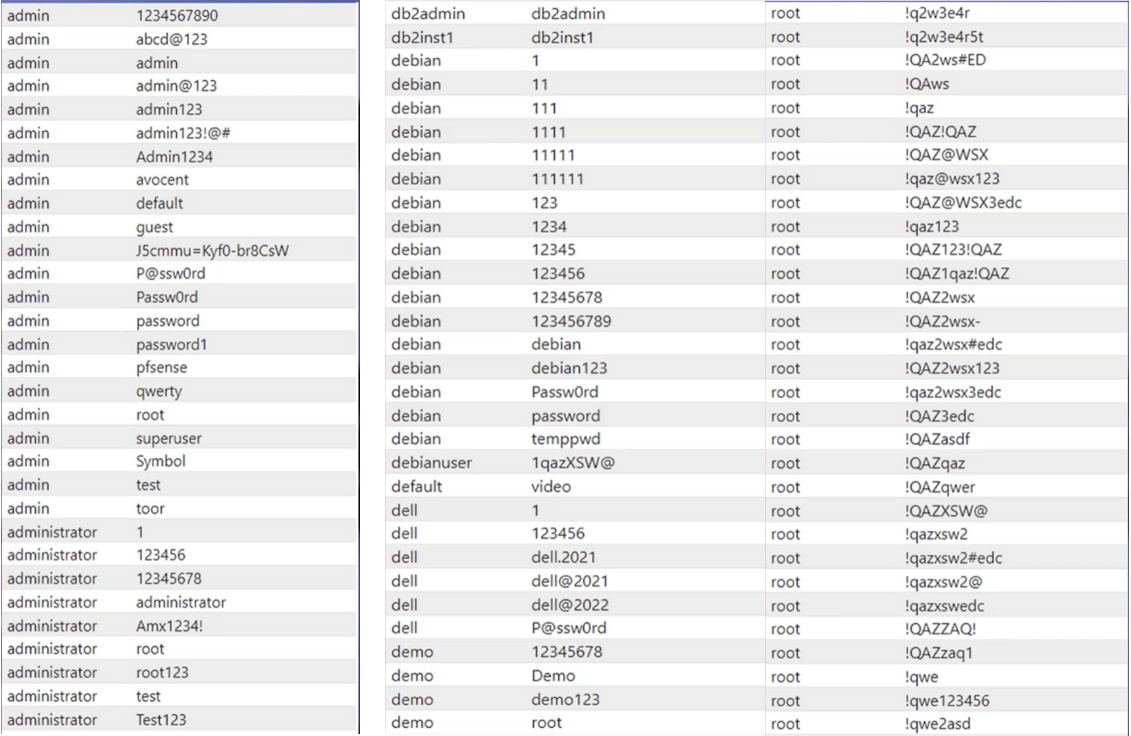
Let's now discover in detail how the attacks are targeting; we can see many logins with different user names like admin, demo, root, etc., and passwords from hacker's password dictionaries.
What Does It Mean for Us?
First, attackers will try to break into the server if we run the server in an internet environment and leave an open connection to our services. Many times I had a chance to see usual misconfiguration like:
- Companies create temporary machines for external access, installed with default configurations and passwords. Usually, this temporary machine is hacked in a few hours or days.
- Or another example is a misconfigured machine for internal users (where security doesn't matter because it is an internal thing), which accidentally exposes it to the Internet. So again, we can see that it's been hacked in a while.
Don't underestimate security configuration and the Internet. Practically you are in the militarized zone there.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What is a cyberattack?
Cyberattack may be defined as any malicious offensive assault targeted against computer network, information system, infrastructure or personal device. It may be attempt by an individual or an organization.
How to prevent cyberattacks?
It is necessary to try to reduce risk by following steps: secure hardware, protect and encrypt data, use security software, educate employees, promote a security-focused culture,...
What are cyber security solutions?
Cyber security solutions consists of tools and softwares that help protect organizations against cyber attacks. It may prevent application downtime, theft of sensitive data, damage to reputation, etc.





