Estimated read time: 5 minutes
A majority of businesses use a range of digital communication options or services, which can make them vulnerable to cyberattacks. In the first quarter of 2021, 39% of businesses reported cyberattack incidents, such as phishing attacks, DDoS attacks, and impersonation, with the medium and large businesses being the most vulnerable.

Security breaches can happen anytime, and when they do occur, they may have costly and damaging repercussions. In the UK, it’s estimated that the average cost of cyber security breaches for businesses ranges from GBP 2,670 to GBP 2.9 million (USD 3.86 million) per incident.Moreover, breaches can lead to financial and data loss, damage to your reputation, and operation or network downtime.
Going on a holiday can be exciting and it can give you some much-needed rest. Unfortunately, cyber attackers don’t take a break. Here’s how you can protect your system from breaches or attacks.
How to Secure Your Systems Before a Long Break
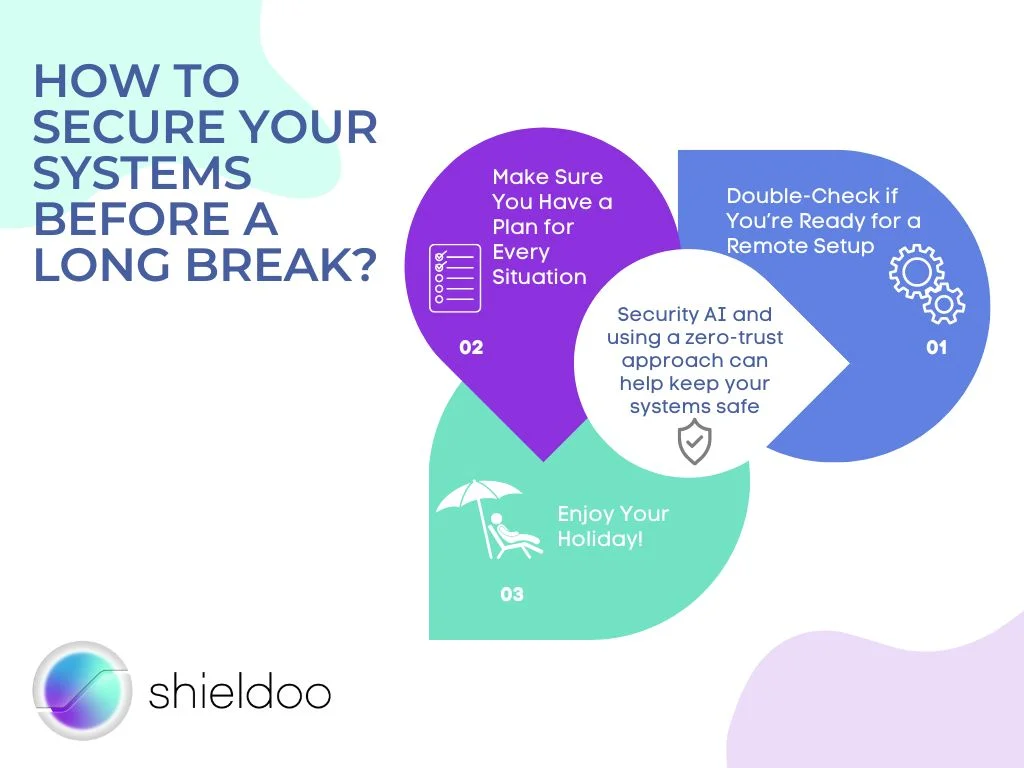
Bolstering your automation and security AI and using a zero-trust approach can help keep your systems safe from attacks and lower the cost of a potential breach. Below are more ways you can ramp up your systems’ security:
1. Double-check if you’re ready for a remote setup
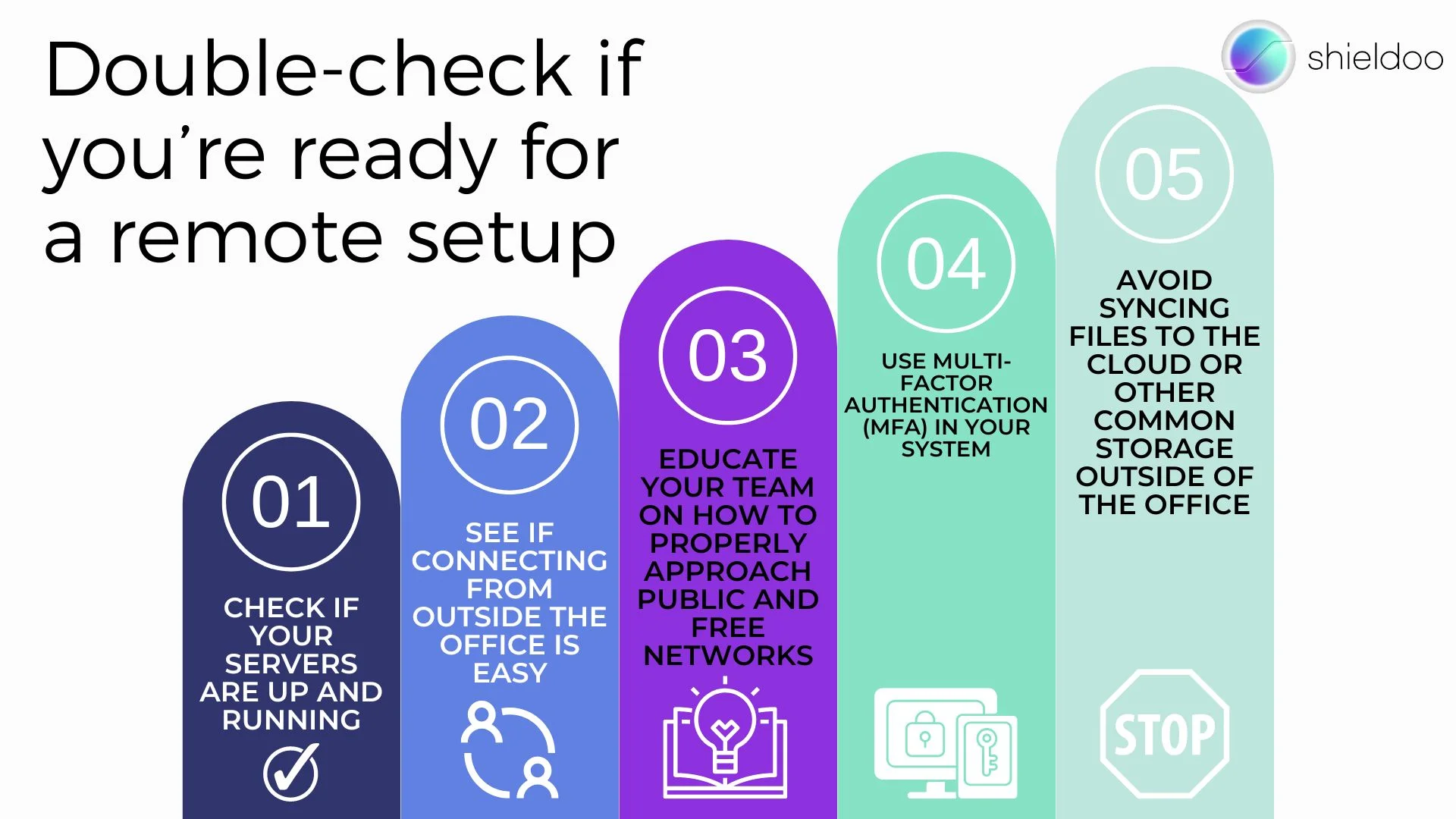
- Check if your servers are up and running
Conduct an audit of your servers and pay attention to crucial components such as their user database and file sharing permissions. With the audit, you can determine their current security capabilities. Additionally, this lets you identify system vulnerabilities, so you can take the appropriate actions to address them.
- See if connecting from outside the office is easy
Determine if you’re able to easily connect to your system remotely so you can still access important data. However, while this is crucial to maintain operations, you still need to build a secure IT system, which means updating or setting up a firewall, implementing physical security for your hardware, backing up your important data or software, and installing a spam filter.
- Educate your team on how to properly approach public and free networks
Keeping your systems safe also means educating your employees about the best practices when it comes to computer security. Before going on a break, have mandatory meetings to emphasize the importance of network security and what they can do to help keep your systems safe, like securing their personal devices and refraining from using public or free networks.
- Use multi-factor authentication (MFA) in your system
MFA fortifies your security measures by requiring users to present proof from two or more authentication categories before they can access your files or systems. In the event of compromised credentials, using multi-factor can hinder cyber attackers, as it would be difficult for them to get through the subsequent authentication factors.
If you’re unable to run an MFA, you can still access your system by connecting through a secure network.
- Avoid syncing files to the cloud or other common storage outside of the office
Using unsecured networks to sync files to the cloud can make your system vulnerable to attacks. If you do need to sync files outside of the office, make sure that your files are encrypted or you’re using secure (encrypted) connections.
2. Make sure you have a plan for every situation
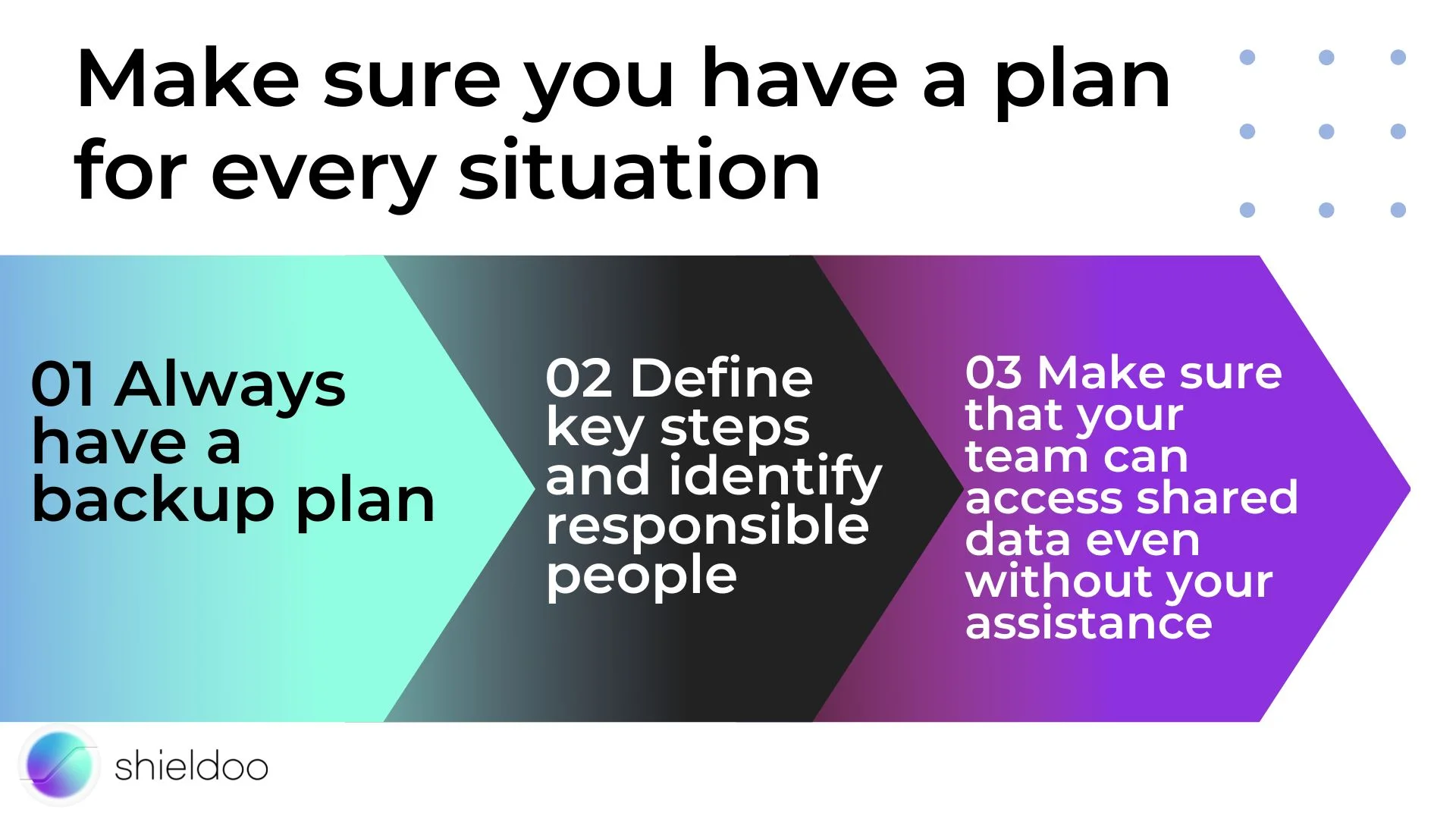
- Always have a backup plan
Despite your best efforts, your systems might still be vulnerable to glitches, which is why you need to have a backup plan for situations such as when your service is down. Identify the risks and assess the impact that such incidents can potentially cause and factor them into your backup plan.
- Define key steps and identify responsible people
You need to create and execute comprehensive IT security policies and standard operating procedures that everyone should follow. Make sure that everyone is aware of these measures and know how to follow the guidelines. You also need to identify the responsible people and what their roles and responsibilities are.
- Make sure that your team can access shared data even without your assistance
While access is important, it’s best to keep track of who can or has access to certain components of your system. If possible, create separate networks for your guests and your employees (main network). For remote access, set up a virtual private network ahead of time so your employees can access shared data securely even without your help.
3. Enjoy your holiday!
Now that you’ve taken measures to protect your system, you can finally have some peace of mind and you can fully enjoy your break.
77% of business and charities prioritize cyber security. Make sure that your business is one of them. The Shieldoo™️ secure mesh lets you work remotely while allowing you to enjoy robust security against cyberattacks. It leverages a zero-trust approach, time-limited access, and traffic monitoring to keep your systems safe.
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
What is security breach?
A security breach is any incident that results in unauthorized access of data, applications, services, networks and/or devices. Security breaches can happen anytime, and when they do occur, they may have costly and damaging repercussions. Moreover, breaches can lead to financial and data loss, damage to your reputation, and operation or network downtime.
How to secure your systems before a long break?
Double-check if you’re ready for a remote setup - check if your servers are up and running, see if connecting from outside the office is easy, educate your team on how to properly approach public and free networks, use multi-factor authentication (MFA) in your system and avoid syncing files to the cloud or other common storage outside of the office.
How to help your coworkers when leaving for a long break?
Define key steps and identify responsible people - you need to create and execute comprehensive IT security policies and standard operating procedures that everyone should follow. Make sure that your team can access shared data even without your assistance - while access is important, it’s best to keep track of who can or has access to certain components of your system. If possible, create separate networks for your guests and your employees (main network). For remote access, set up a virtual private network ahead of time so your employees can access shared data securely even without your help.





