Estimated read time: 8 minutes
Today’s work environment is moving past the four walls of offices as more businesses undergo digital transformation and adopt cloud computing. Employees can deliver work from home, or just about any corner of the world.
The increased number of devices and users logging in to your business network poses a significant risk of exposing sensitive data to prying eyes, and the network security perimeter you have may just not be enough. Zero Trust security revolutionizes IT infrastructure with rigorous identity verification for easy management of data breaches and cybersecurity threats.
What is Zero Trust?
The Zero Trust security model adheres to the philosophy that no user, device, or connection is to be trusted. Location is not relevant to Zero Trust whether you are inside or outside the network.
A traditional security model would grant access to users based on their proximity to the network. Because the security infrastructure recognizes the connection from previous access requests, the user or device can have access to all data, services, or applications within the network. They can move freely across the network. However, as malicious intent is becoming more prevalent on the cloud, the lack of security checkpoints puts a network’s critical data in danger.
The Zero Trust approach replaces the archaic security infrastructure, employing advanced security protocols, risk analysis, and management plans to protect business and private networks from data breaches.
With a Zero Trust security posture, no user, device, or third-party application is trusted by default. Cloud computing platforms are where Zero Trust is commonly applied due to their accessibility across multiple devices. However, a Zero Trust framework can be deployed in a local network or a hybrid between local and cloud networks.
The Benefits of Zero Trust Security
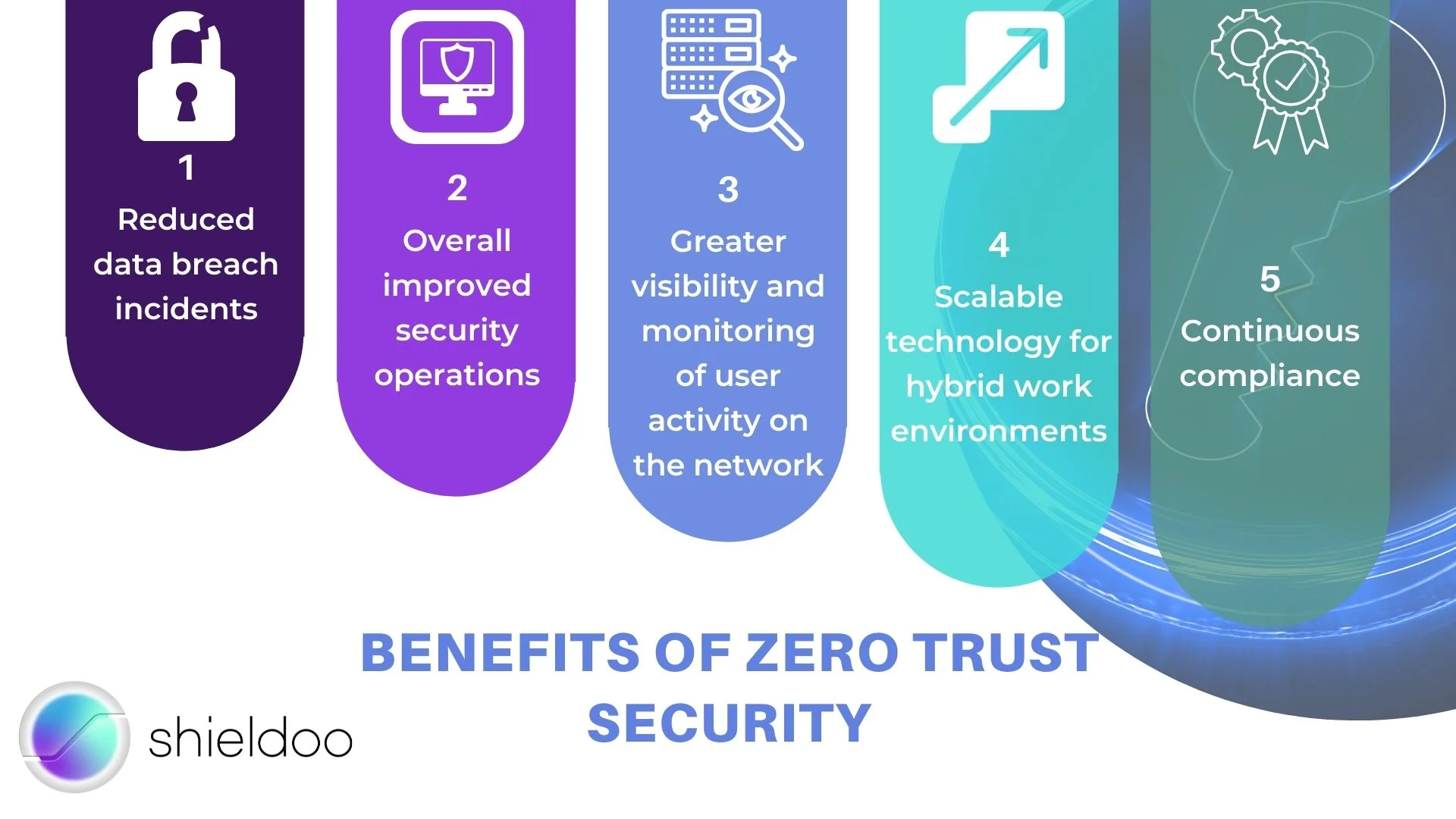
1. Reduced data breach incidents
Data breaches are among the stifling concerns of the IT department. While external threats are becoming more advanced, insider threats aggravated 94% of organizations in 2021 alone. Human error is revealed to be the cause of data breaches from within a network for 84% of organizations. These mistakes can vary, from accessing company sensitive data on a public network or mobile device or using unauthorized IT solutions.
With a Zero Trust security model, the IT department can tighten security and automate verification and user identification for every resource that a user requests access to. Insider breaches are prevalent because traditional IT infrastructure lacks the scalability from a local to a cloud network. Organizations can adopt and scale Zero Trust across platforms and implement advanced access management and multi-factor authentication to address insider threat incidents. Extracting data is also locked behind rigorous verification procedures to prevent accidental disclosure of critical information.
2. Overall improved security operations
An outdated security network perimeter tends to provide anonymity on the Internet but falls short of security features for the IT department to utilize for more efficient operations. Zero Trust security solves this with a stack of advanced security tools. Thus, an IT department can monitor user activity on a private network efficiently.
3. Greater visibility and monitoring of user activity on the network
55% of IT security teams and departments rely on the initiative of employees to report suspected and/or confirmed information breaches. Before Zero Trust security, there is barely a reliable method for IT to keep track of all user activity occurring on the network. IT teams are incapable of apprehending shadow IT solutions or malicious activity without the proper tools.
Zero Trust network security empowers the IT department by granting them improved monitoring capacity for user activity within the network. The ever-evolving yet automated AI of Zero Trust analyses user behavior and delegates verification checks when necessary.
4. Scalable technology for hybrid work environments
The COVID-19 pandemic has highlighted the significance of flexible work setups to improve or maintain productivity within an organization. It is inevitable for security measures to loosen as businesses find the balance between managing data locally and on the cloud.
Hardware-based security solutions require extensive upgrades for employees to access the business network from a “secure” access point. The security level is also limited with such infrastructure. Virtually any device with credentials validated by the network can access and extract information as the user pleases, increasing the risk of insider data breaches.
Zero Trust architecture addresses the issue of scalability. As it is not tethered to any hardware, Zero Trust can be implemented in small to large-scale networks. Users can request data from the office or from their living rooms. Regardless of user location, Zero Trust is implemented to authenticate and verify user, device, and behavior across the network.
5. Continuous compliance
A Zero Trust network security model makes it manageable for a business to perform and produce results according to regulatory requirements and standards. The automated verification checks and analysis reports on the activity within the network keep the IT department informed on concerns vulnerable to cyberattacks. Taking on pre-emptive measures allows businesses to minimize damages that may easily cost them millions of dollars if left unattended.
The Core Principles of Zero Trust Security
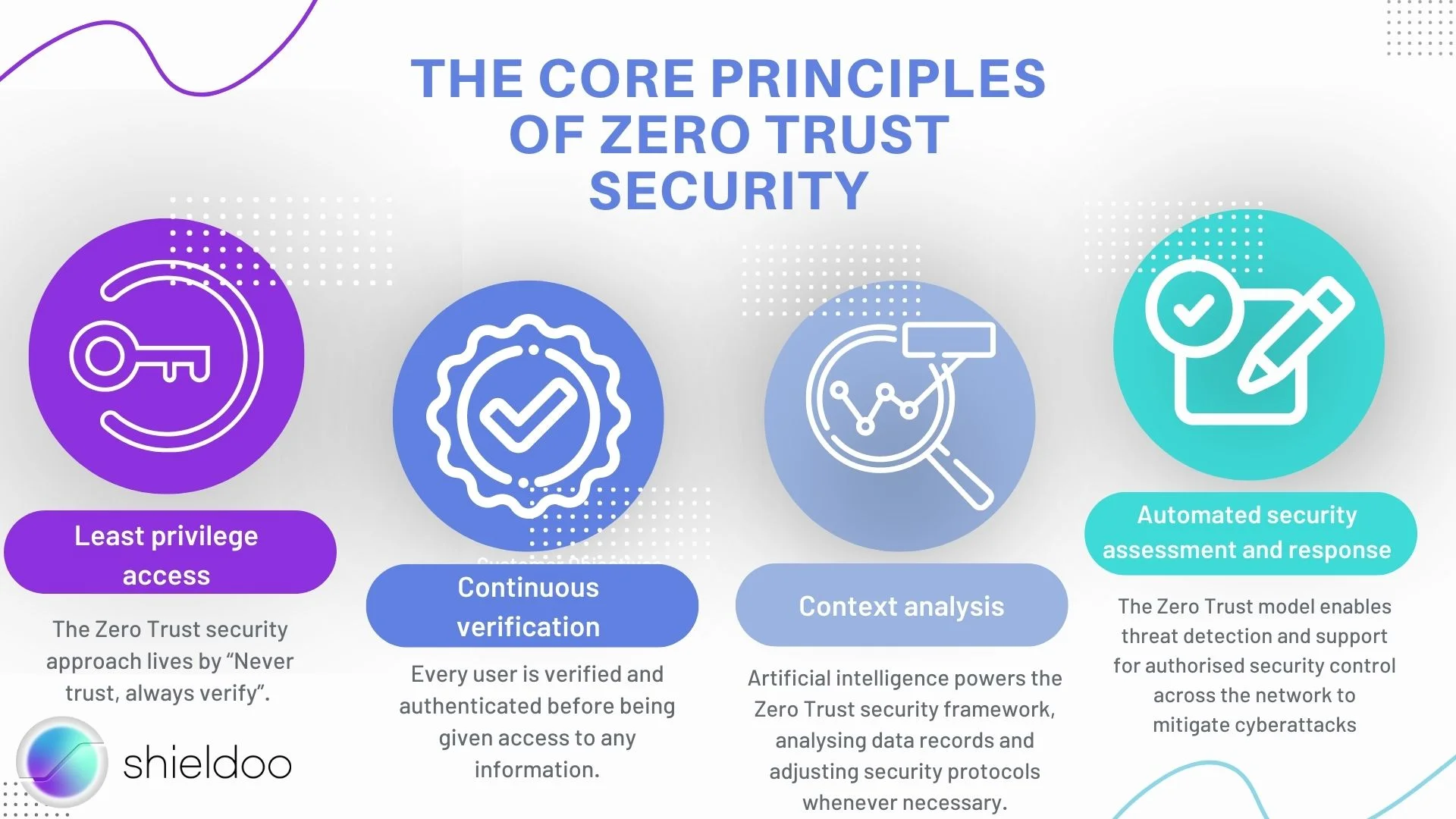
1. Least privilege access
The Zero Trust security approach lives by “Never trust, always verify”. Users may request to connect to a network, but this does not grant the user access to other resources and applications within the network. Zero Trust security employs user authentication for every new connection attempt or access request to a private network.
2. Continuous verification
Zero Trust and granular data protection require user identification and device authorization to validate the identity and reason for the user’s access request. User identity and intent for accessing information are constantly verified and authenticated. Rigorous verification ensures that no suspicious activity breached its way through the network.
3. Context analysis
The Zero Trust model analyses and reviews user behavior and changes in network activity to detect suspicious activity or malware that has breached the network. Traditional IT security posture relies on human intelligence to notify the IT department of any malicious activity. Artificial intelligence powers the Zero Trust security framework, analysing data records and adjusting security protocols whenever necessary.
4. Automated security assessment and response
The Zero Trust model enables threat detection and support for authorized security control across the network to mitigate cyberattacks. The IT department can streamline security checkpoints, authentication procedures, and the like without relying on external security applications.
The Zero Trust Architecture

At the core of the Zero Trust network architecture is “Never trust, always verify”. Traditional security perimeters and the “Trust, but verify” principle can put organizations at a disadvantage as insider threats become the top cause of data breaches and cyberattacks.
Zero Trust architecture implements strengthening a network’s security measures through rigorous user verification and authentication and granting least privilege access to all users regardless of their position within the business network. From attempting a connection to navigating their way inside the network, users have to verify their identity and intent for accessing critical data.
Zero Trust and least privilege access allow users to extract data at the minimum. This means they can only access one resource at a time. Should they need to access another application, they will have to request permission once again. Such network segmentation of the Zero Trust architecture prevents lateral movement and mitigates internal data breaches.
Implicit vs. Explicit Trust
The Zero Trust model employs an explicit trust solution, opposite to that of a perimeter-based security strategy. Every new user, device, or application requesting to connect to a Zero Trust network has to undergo rigorous verification throughout the session.
What is Zero Trust Network Access?
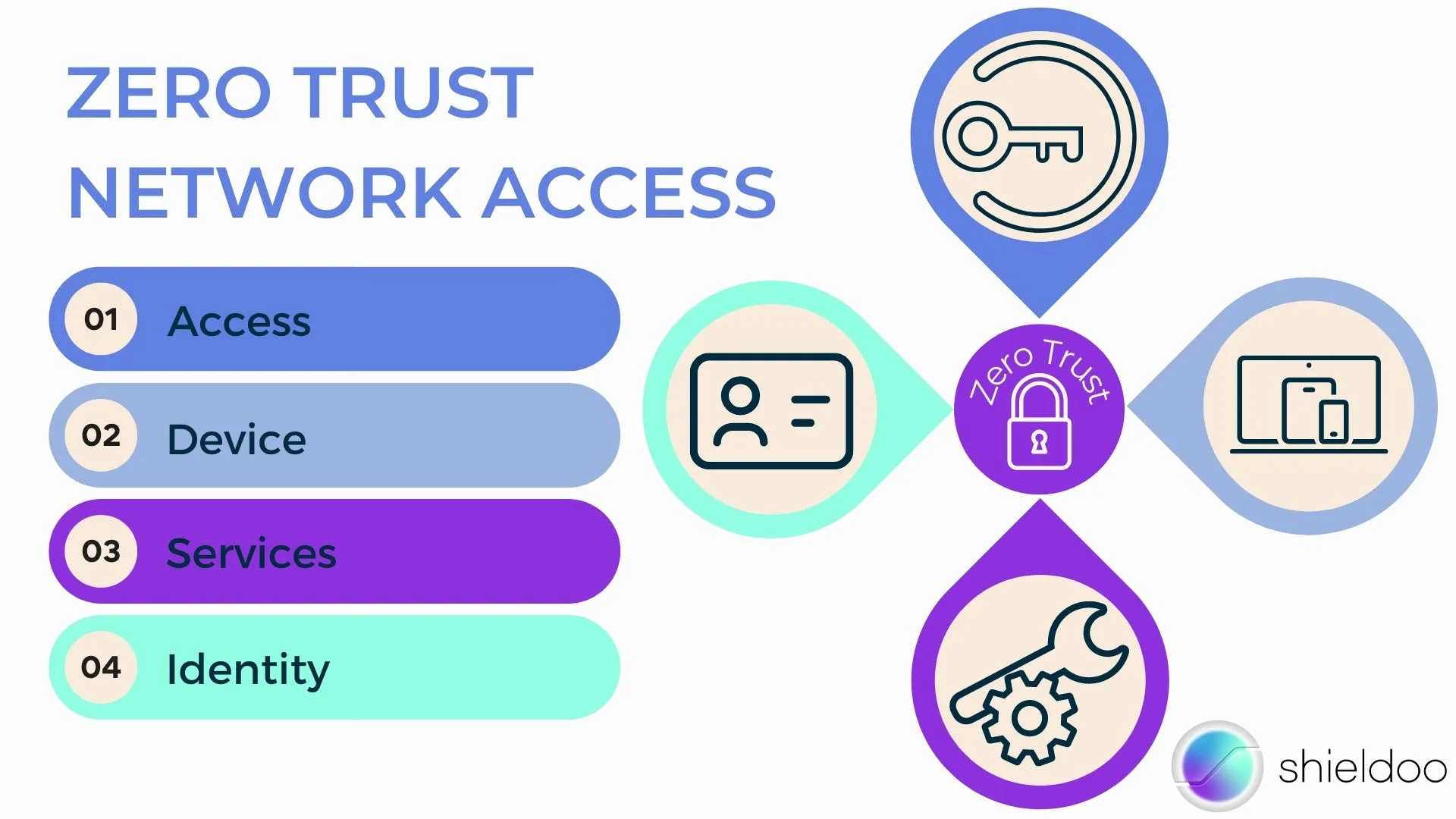
The Zero Trust Network Access is a technology granting access to data on the network on a case-by-case basis. With ZTNA, verifying user identity and authenticating devices are crucial for signing into the Zero-Trust network.
Benefits of ZTNA for Businesses
- Flexible security support across local, cloud, or hybrid workforces
- Scalable and software-based, does not require hardware upgrades to broaden the network perimeter
- Meets regulatory requirements and compliance standards for a secure and stable IT infrastructure
- Protects enterprise data at a granular level
Benefits of ZTNA for IT
- Greater visibility of device health and user activity
- Reduced risks brought by shadow IT
Try Shieldoo™️
Cyber security is becoming more and more important, which is why we provide you with essential information in a wide variety of articles on our blog. We also developed a new tool Shieldoo™️ based on Nebula from Slack which can help you to provide secure connection between end-users and servers. You can try your own private network here.
FAQs
How does ZTNA differ from SDP?
ZTNA and SDP are terms often used interchangeably. A software-defined perimeter (SDP) is the software solution for an organisation’s network to adopt ZTNA.
Why is ZTNA important?
With ZTNA, critical assets and valuable resources can be protected from prying eyes. Digital transformation in the workplace maximises ZTNA. Businesses no longer have to worry about their most critical assets because of the rigorous user identity verification that Zero Trust implements every time a user requests access to new data or logs in on a new, unrecognised device.
How do I build a Zero Trust Network?
A Zero Trust network is reliant on the significance and value of resources available within the network. To establish your Zero Trust strategy, determine the security level necessary to protect enterprise data and valuable data on the network.Identifying the userbase comes next. This adds context as to which network resources, services, and the applications users access. This will also help craft the best policies on Zero Trust security and access management to resources like customer data, intellectual property, and services on the Zero Trust network.
Is ZTNA part of SASE?
ZTNA is a small yet significant part of the secure access service edge (SASE). SASE is another security solution comprised of services such as ZTNA, secure web gateway, and cloud access security.Whereas ZTNA authorizes users and devices to connect to a corporate or private network, SASE is a bigger security model that further contextualizes the ZTNA procedure. With SASE, ZTNA can detect suspicious activity and inform the IT department on which users or IP addresses to add to the block list.
ZTNA vs. VPN: Which is better?
Zero Trust Network Access offers strong authentication and continuous monitoring. VPN is held back by its hardware-based capacities and the universal access to the resources on the network. Once users are granted access through a VPN, they have the liberty to access data stored in the entire network.





