ZTNA (Zero Trust Network Access) is a network environment where all resources are hidden, and the user is getting access only to specific resources. In contrast to classical firewalling, we mean a particular web service and not just IP or port by a resource. This approach often has some pre-requisites like MFA and is granted only for a specific time window.
The Zero Trust security model adheres to the philosophy that no user, device, or connection is to be trusted. Location is not relevant to Zero Trust whether you are inside or outside the network.
A traditional security model would grant access to users based on their proximity to the network. Because the security infrastructure recognizes the connection from previous access requests, the user or device can have access to all data, services, or applications within the network. They can move freely across the network. However, as malicious intent is becoming more prevalent on the cloud, the lack of security checkpoints puts a network’s critical data in danger.
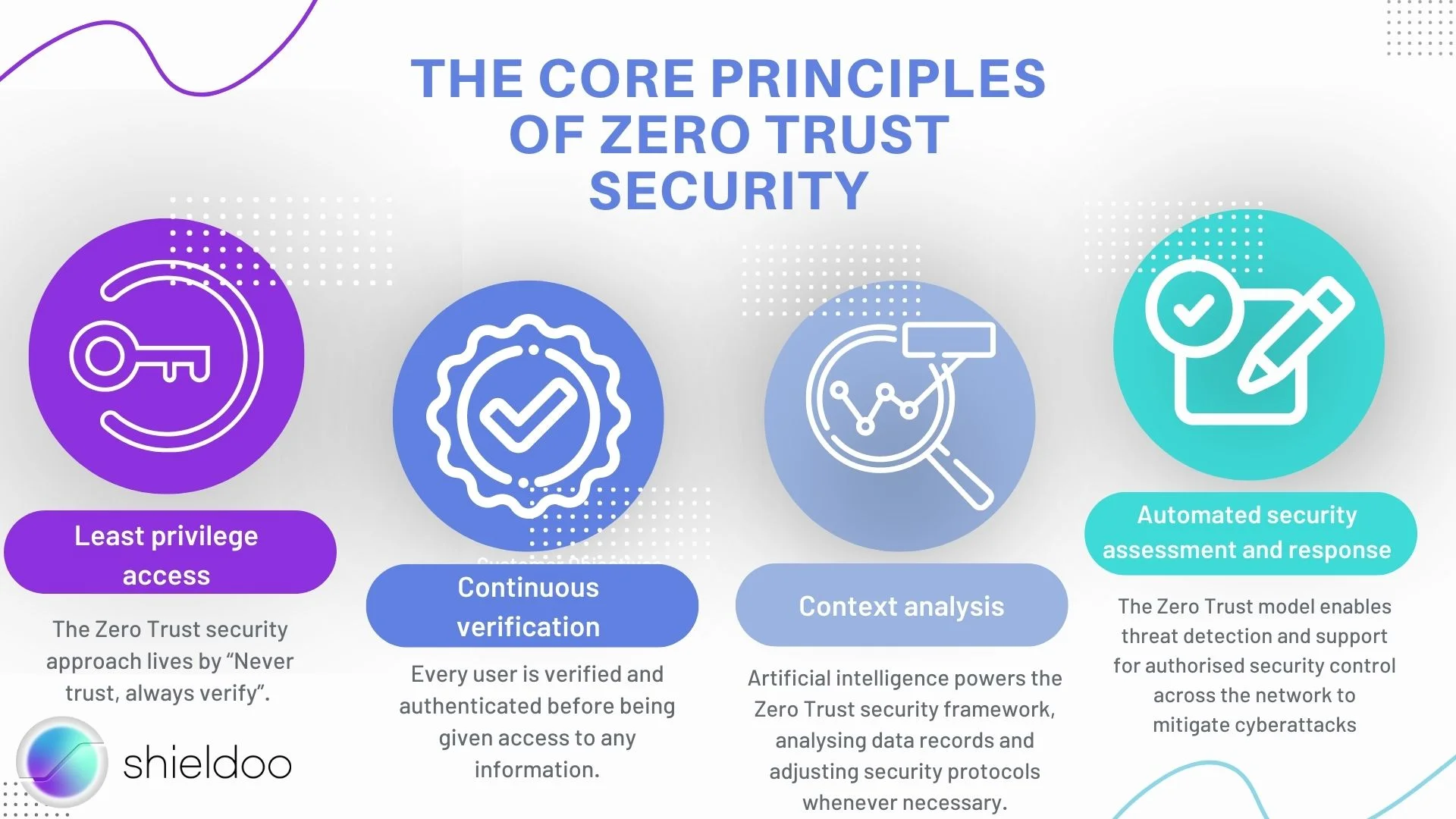
The Zero Trust approach replaces the archaic security infrastructure, employing advanced security protocols, risk analysis, and management plans to protect business and private networks from data breaches.
With a Zero Trust security posture, no user, device, or third-party application is trusted by default. Cloud computing platforms are where Zero Trust is commonly applied due to their accessibility across multiple devices. However, a Zero Trust framework can be deployed in a local network or a hybrid between local and cloud networks.
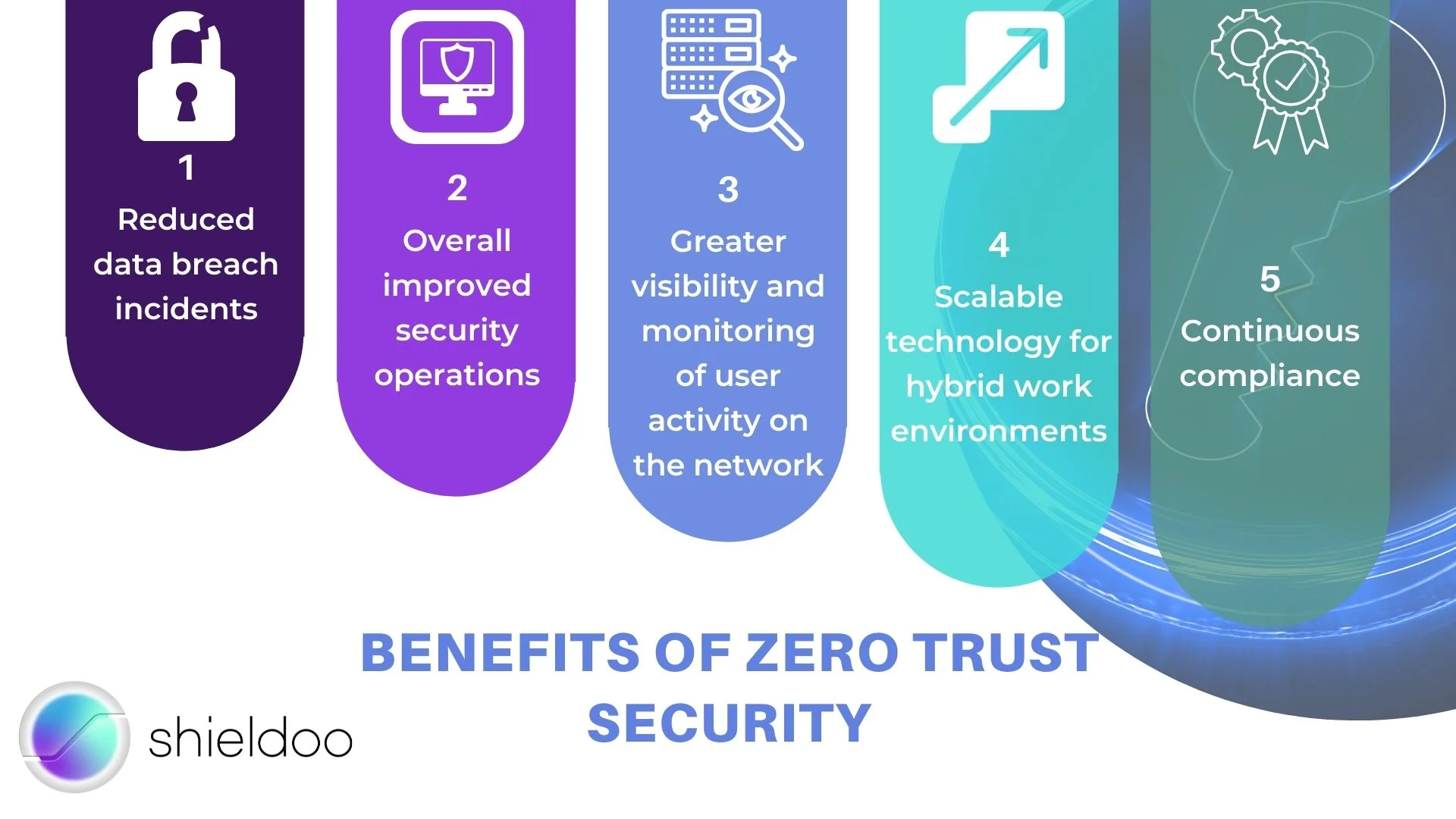
Read more in the article Zero Trust Security to Reinvent Your Cybersecurity
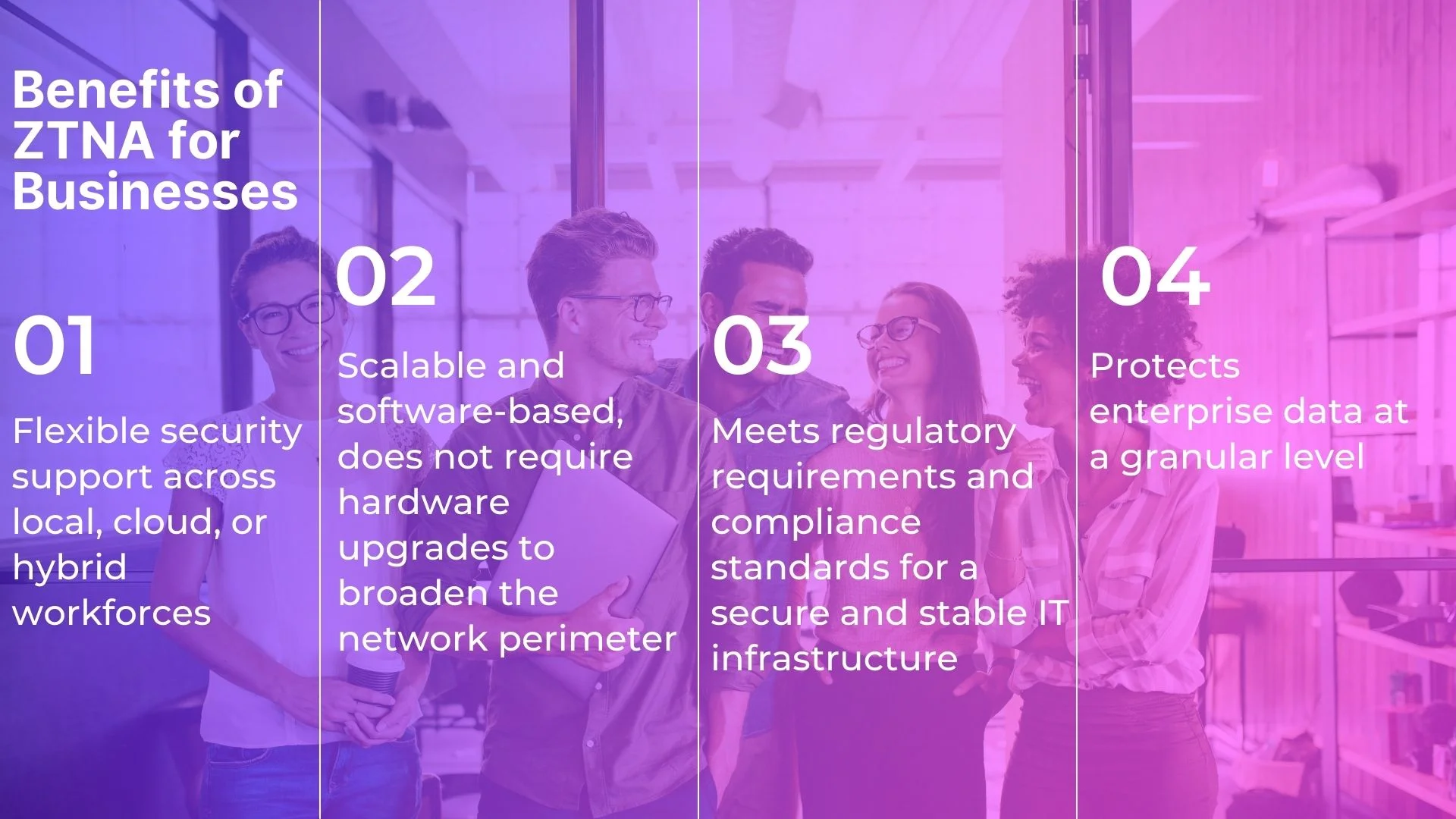
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
diam libero
The mesh is a collection of nodes, a lighthouse, and an admin center. The user device is a node, a server is a node, cloud stack is a node, LAN access box is a node.




